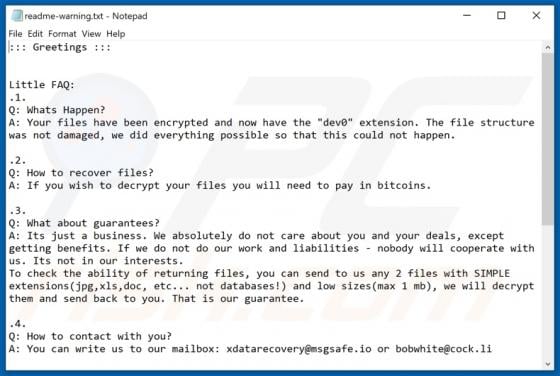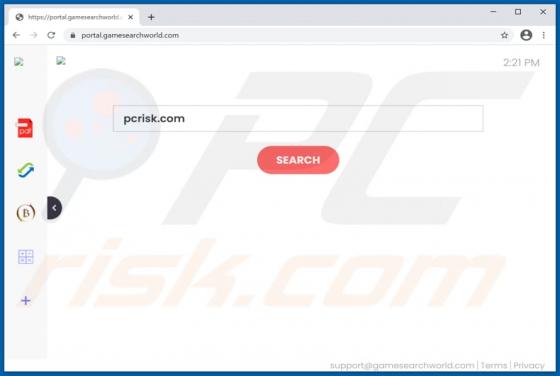
GameSearchWorld Browser Hijacker
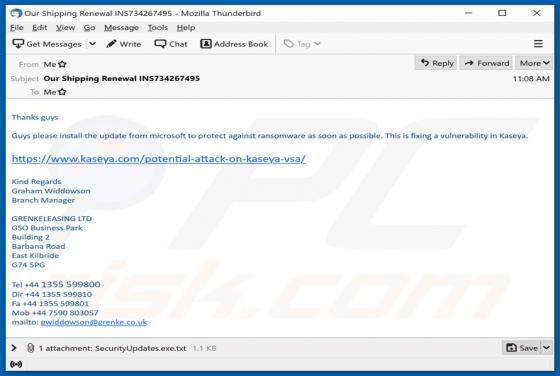
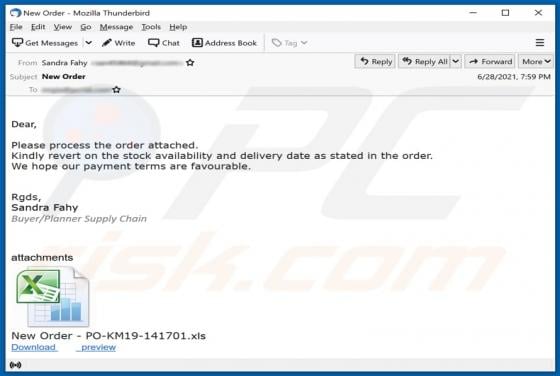
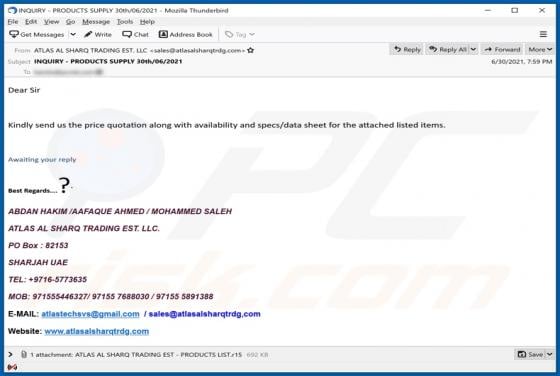
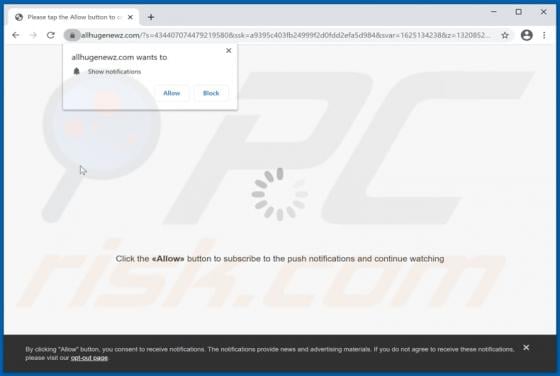
GameSearchWorld is a browser hijacker designed to promote the gamesearchworld.com address. Gamesearchworld.com is a fake search engine that does not generate any unique results. Most users download and install browser hijackers unintentionally. Therefore, apps of this type are called potentially u