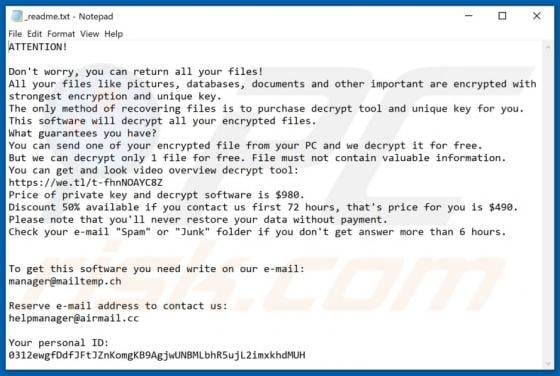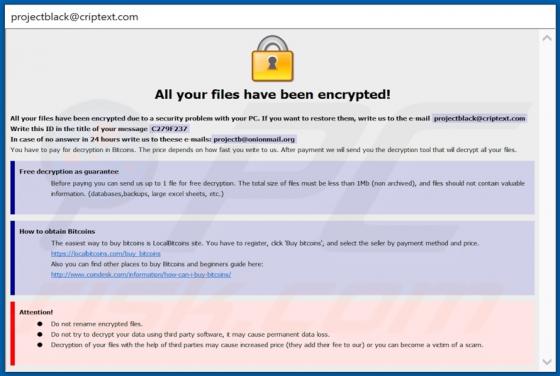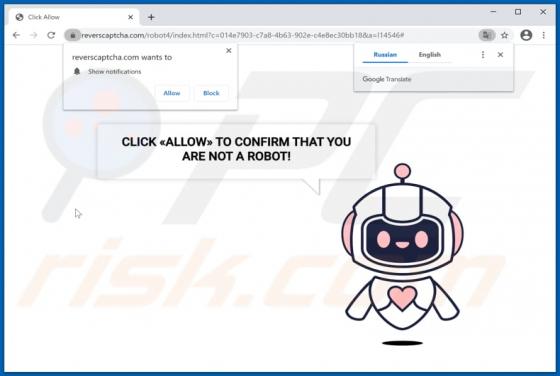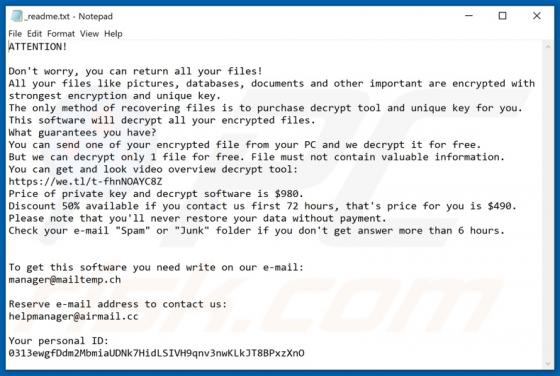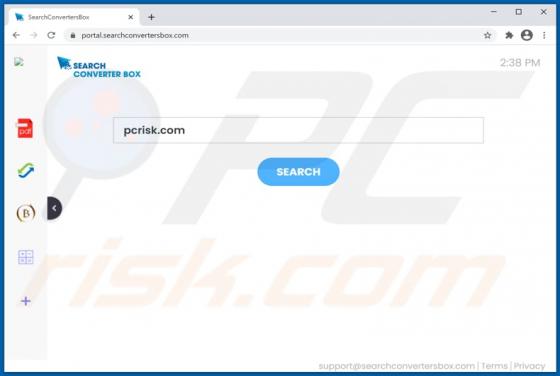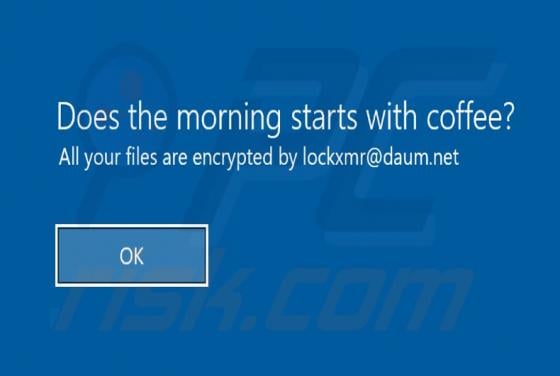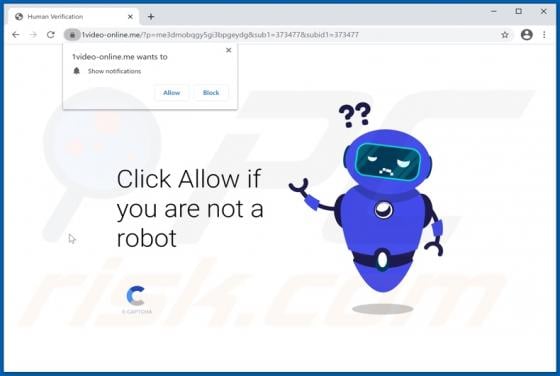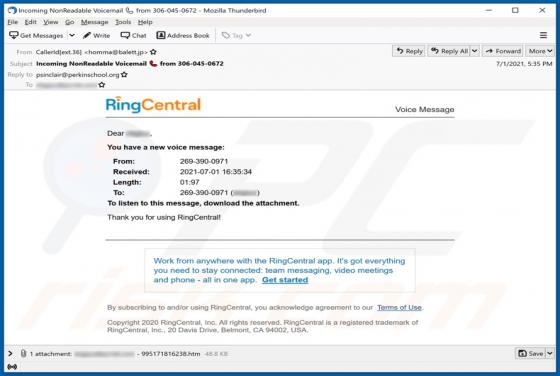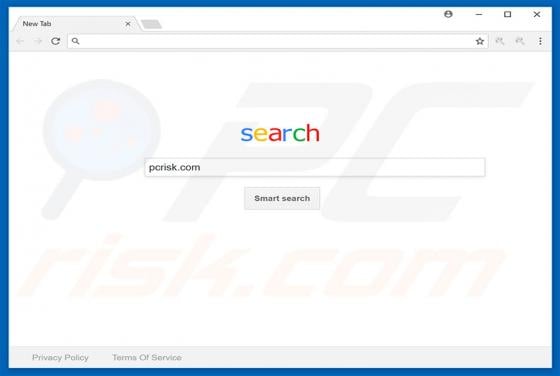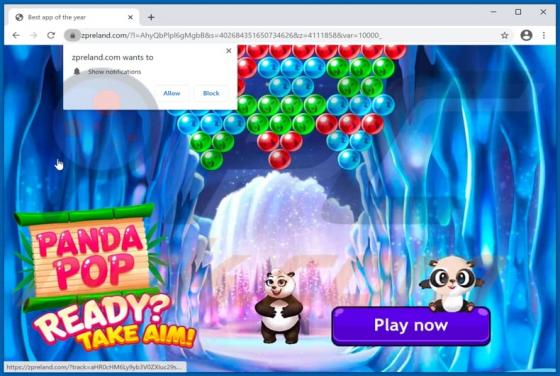
Zpreland.com Ads
Zpreland[.]com is an untrustworthy website that checks the IP address of its visitors and then loads its content or opens a couple of other websites of this kind. It is worth mentioning that it is uncommon for pages like zpreland[.]com to be visited intentionally. Usually, websites like zp