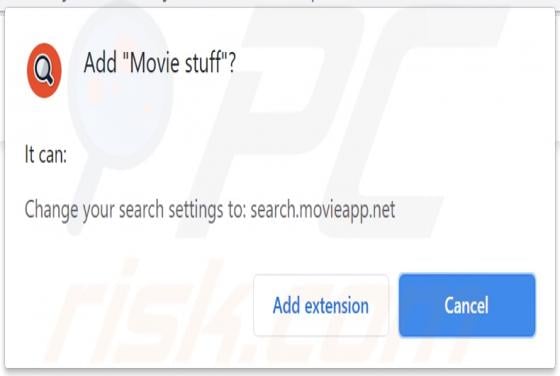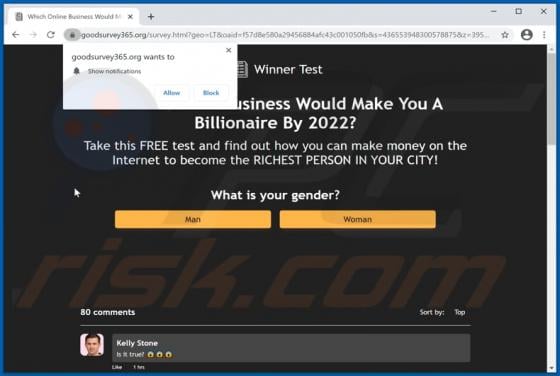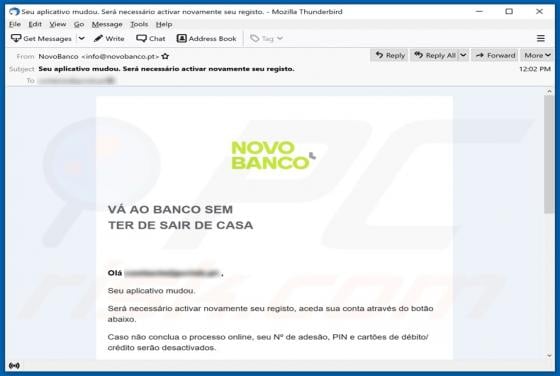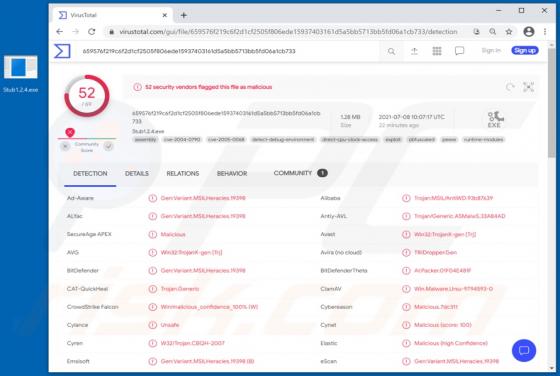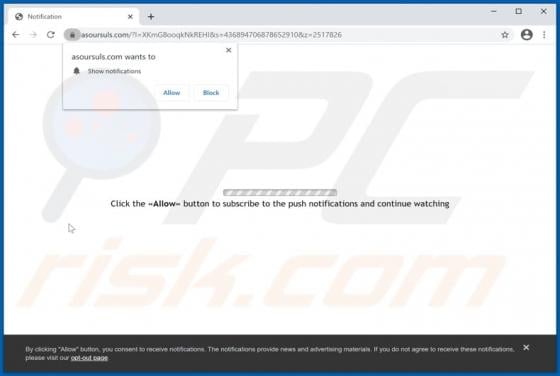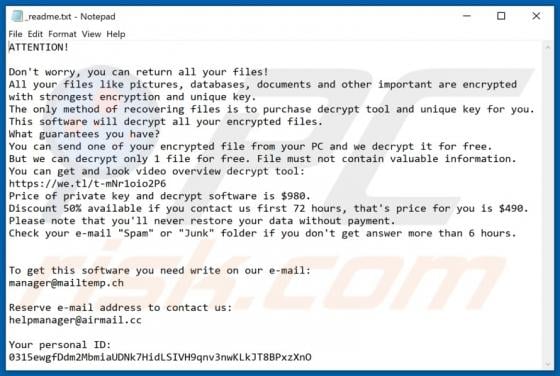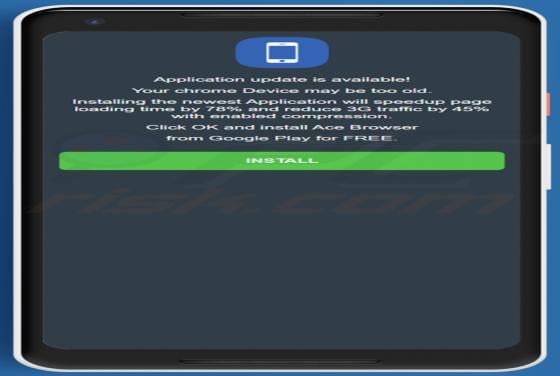
Your Chrome Device May Be Too Old POP-UP Scam (Android)
"Your chrome Device may be too old" is a scam targeting Android device users. This scheme is promoted on various deceptive websites. The scam informs that an application update is available, which is recommended as the users' devices are likely outdated. Typically, scams of this type proliferate