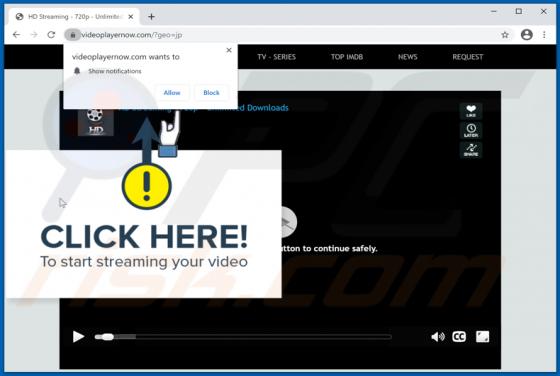
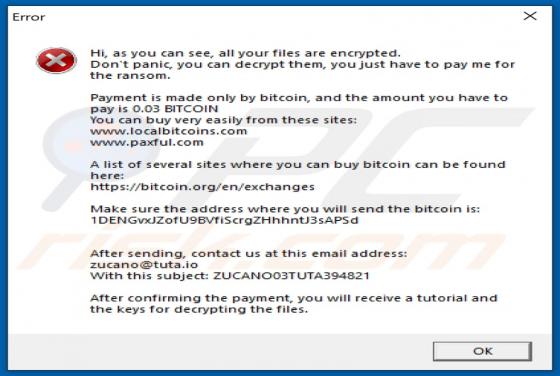
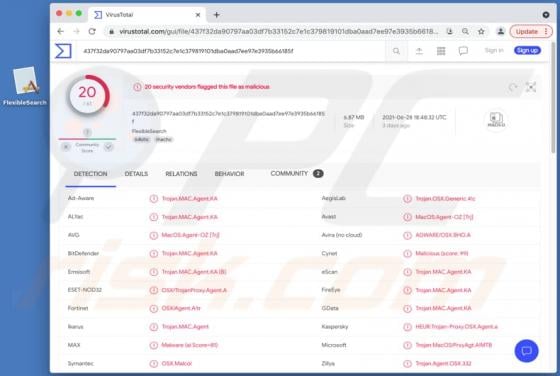
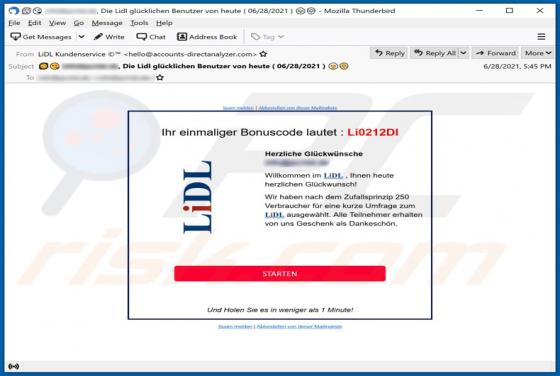
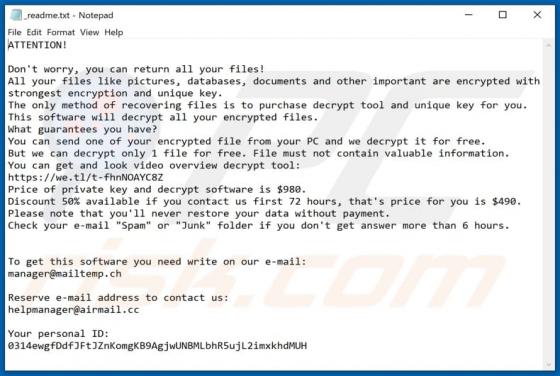
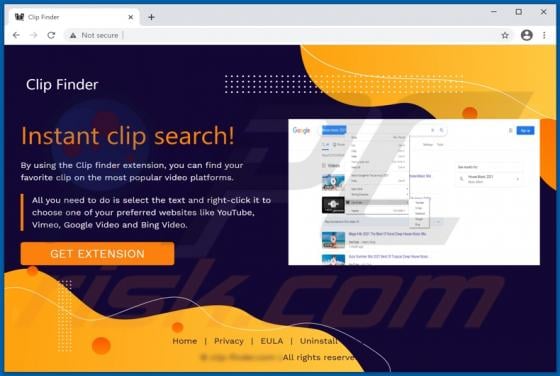
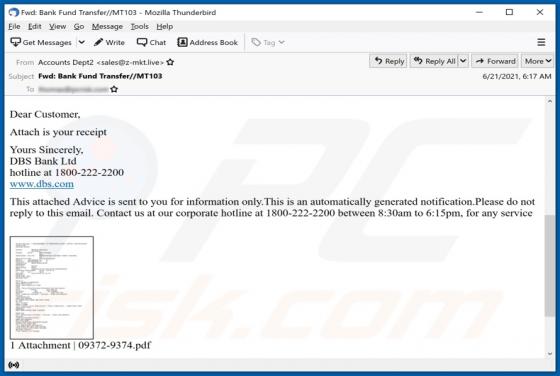
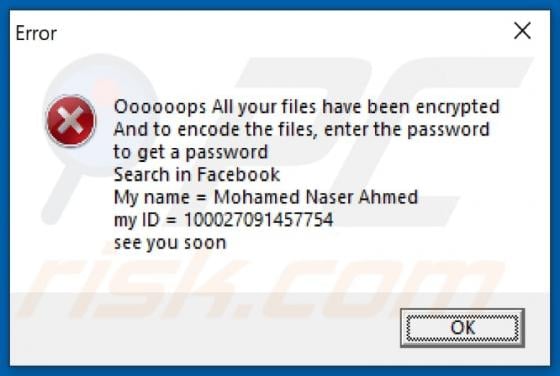
IndexerProject Adware (Mac)
IndexerProject is a piece of rogue software categorized as adware. It also has browser hijacker qualities. Following successful installation, this app runs intrusive advert campaigns and promotes fake search engines (through modifications to browser settings). Additionally, IndexerProject has d