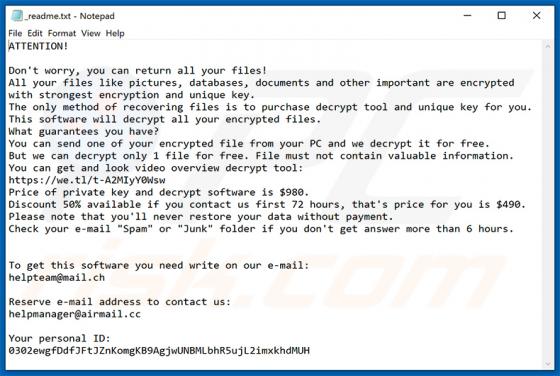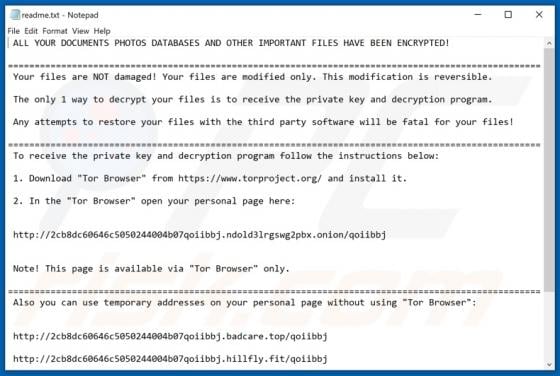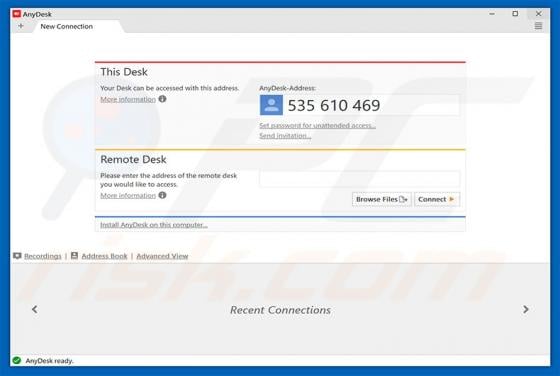
AnyDesk Virus
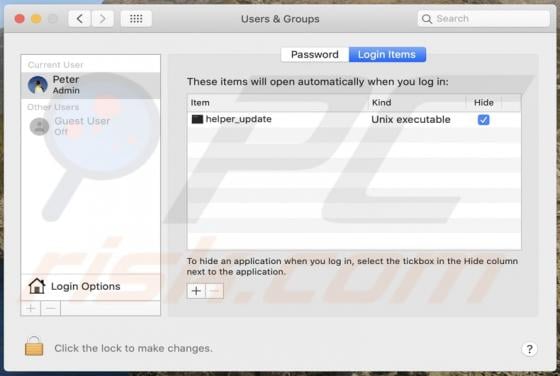
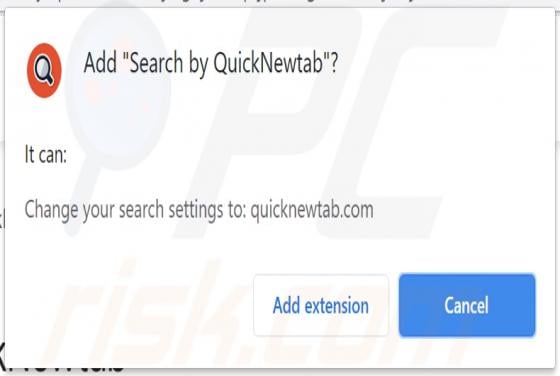
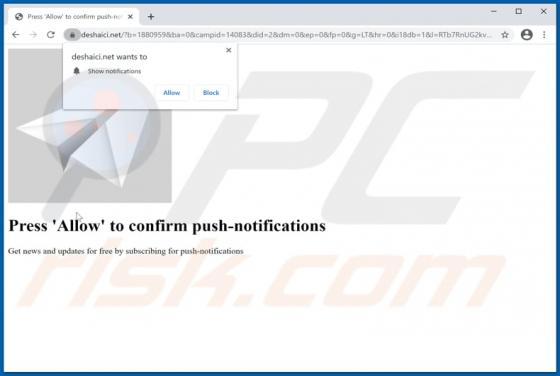
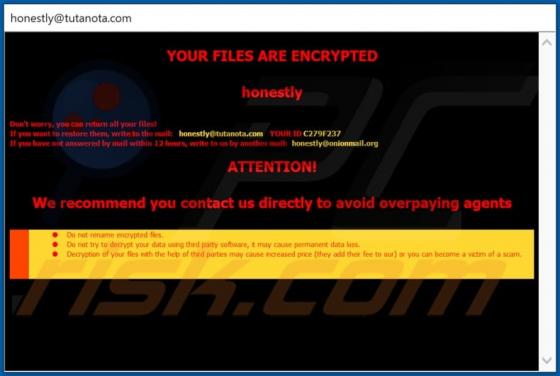
Similar to TeamViewer, AnyDesk, is a legitimate application that provides remote system control functionality. Recently, however, cyber criminals have started distributing a modified version of AnyDesk using the "bundling" method, and thus it typically infiltrates without users’ permission.