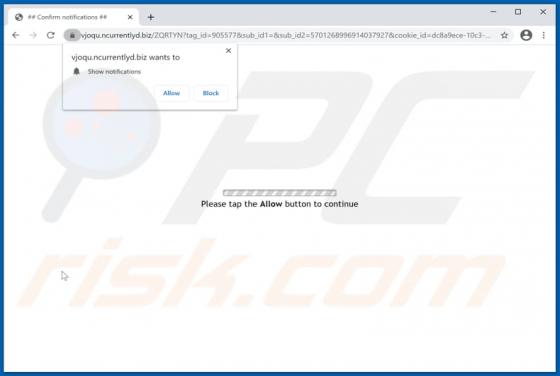
Ncurrentlyd.biz Ads
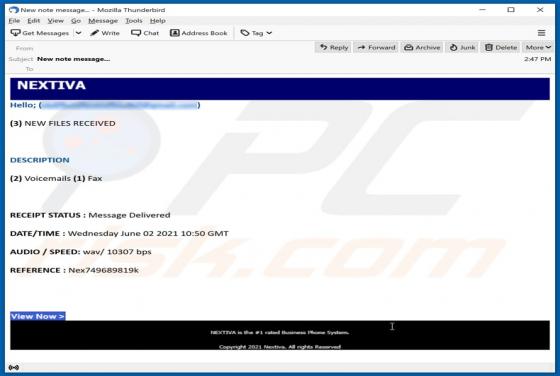
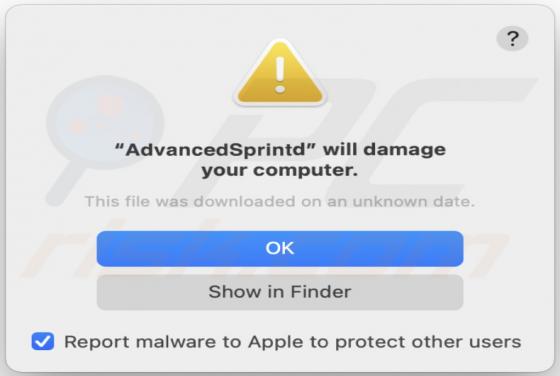
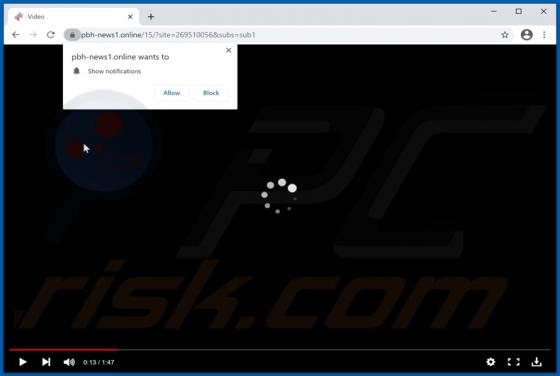
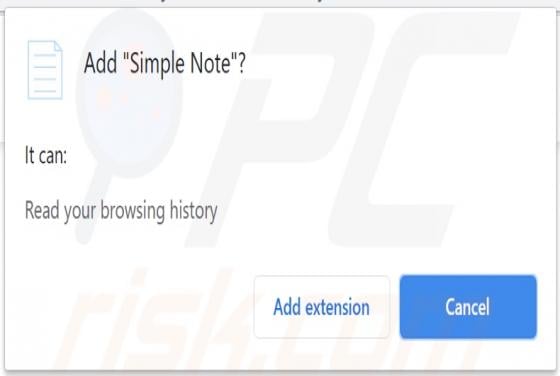
Ncurrentlyd[.]biz is an untrustworthy page designed to promote other untrustworthy, potentially malicious websites and load deceptive content (its functionality depends on the geolocation of a visitor). It is important to mention that pages like ncurrentlyd[.]biz are rarely visited intentionally.