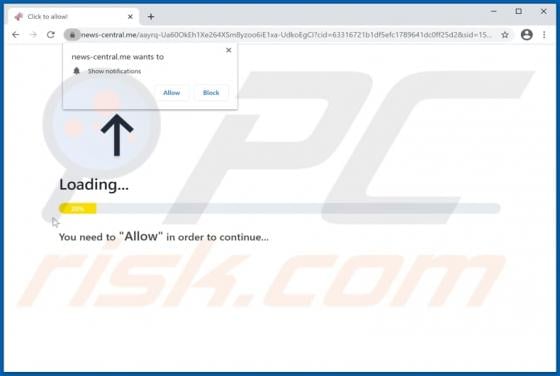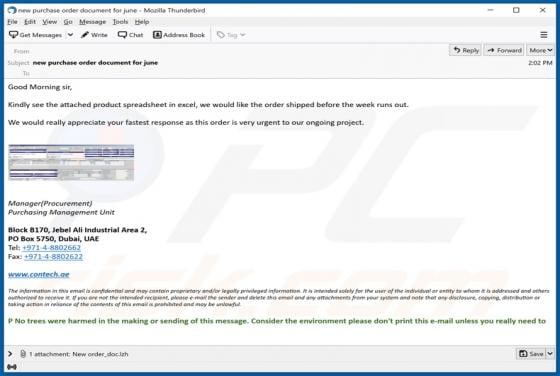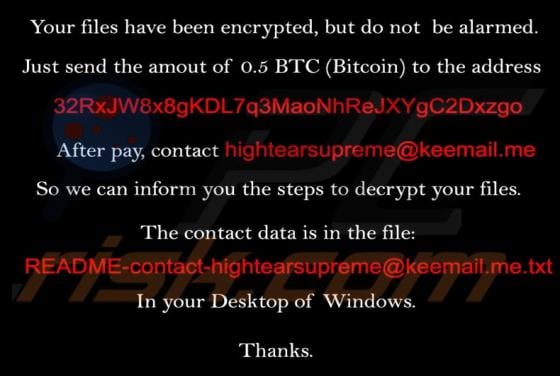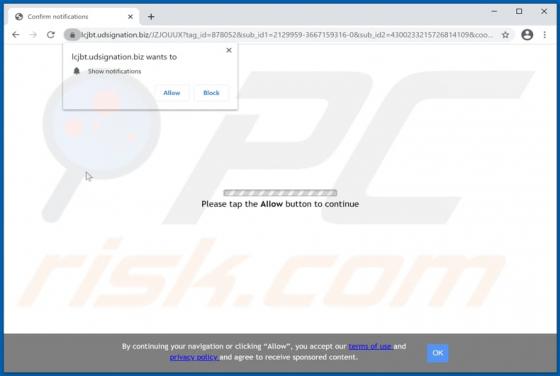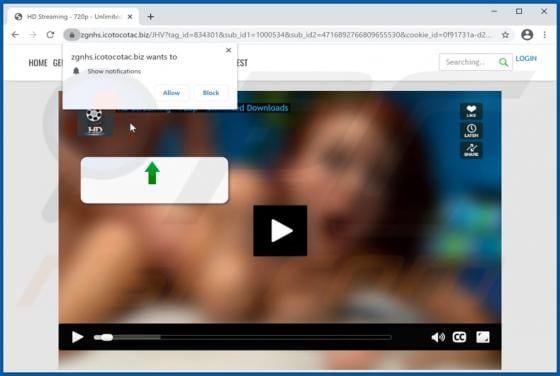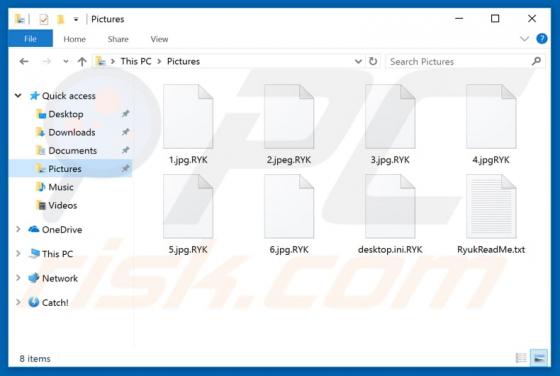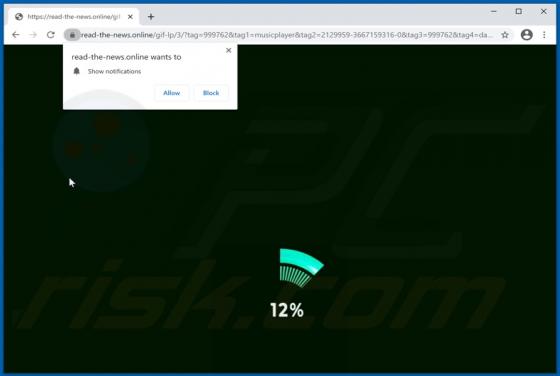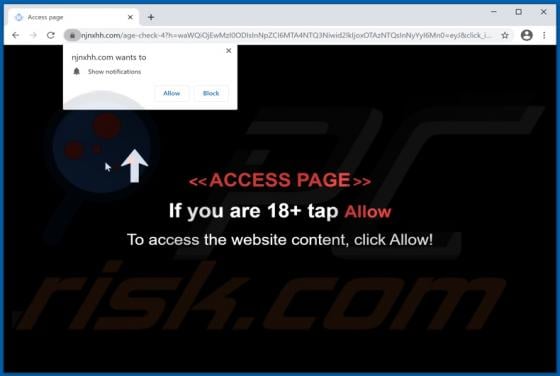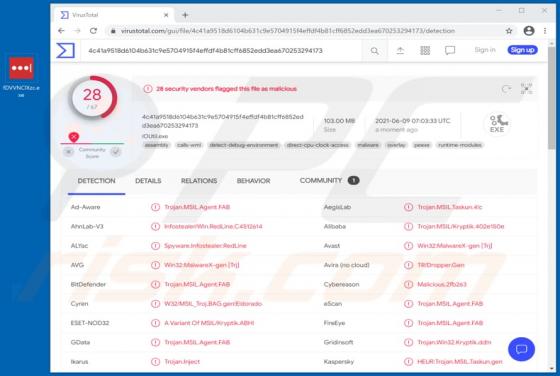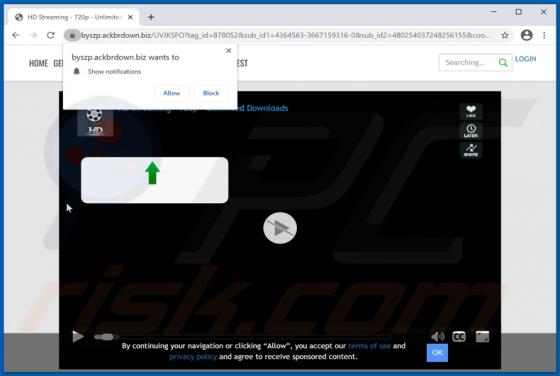
Ackbrdown.biz Ads
Ackbrdown[.]biz is yet another rogue webpage. The Internet is full of such untrustworthy and harmful sites; news-central.me, udsignation.biz, read-the-news.online - are but a few examples. Websites that are classified as rogue operate by loading questionable content and/or redirecting their visit