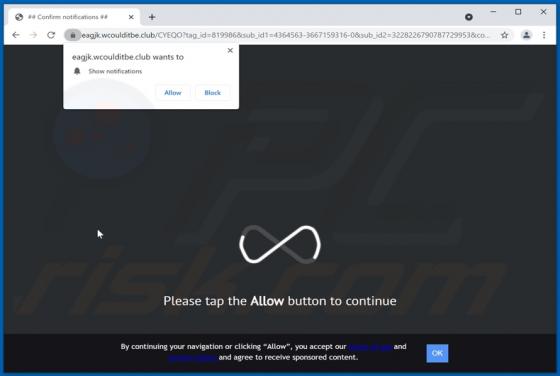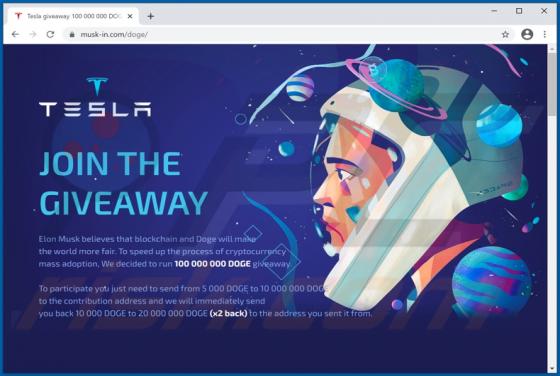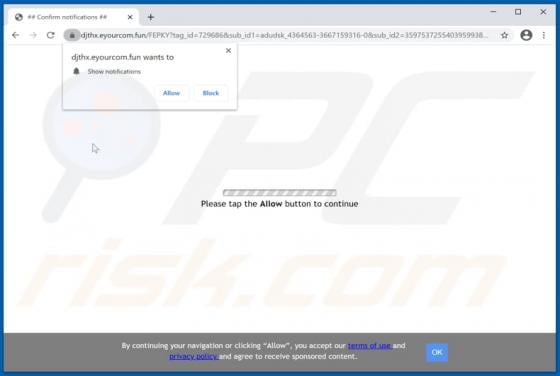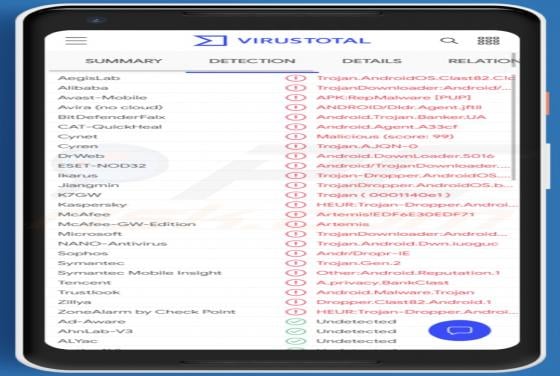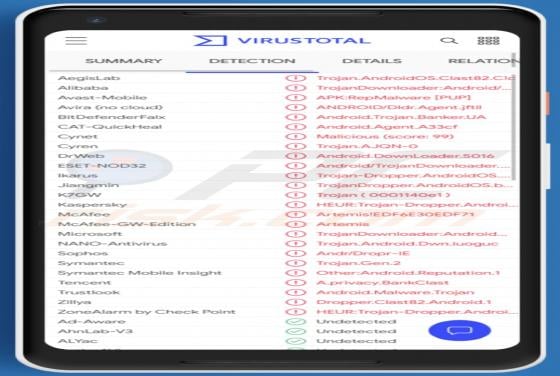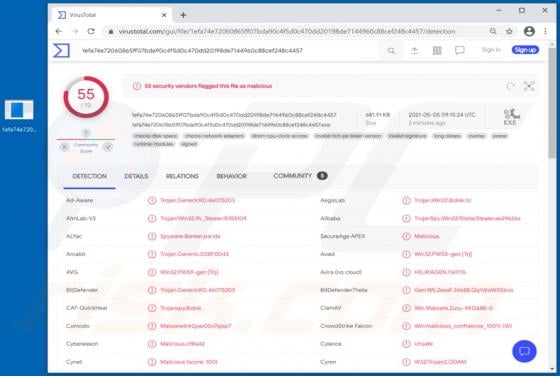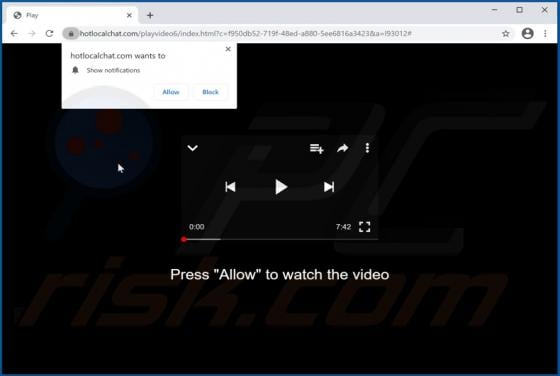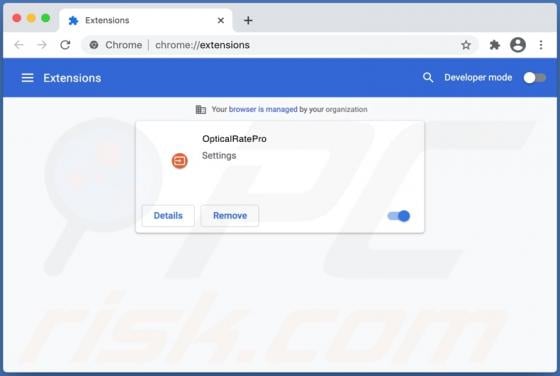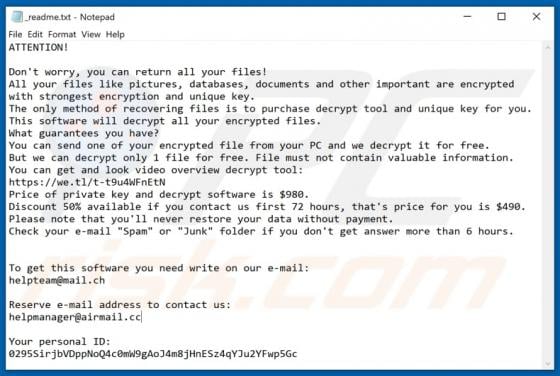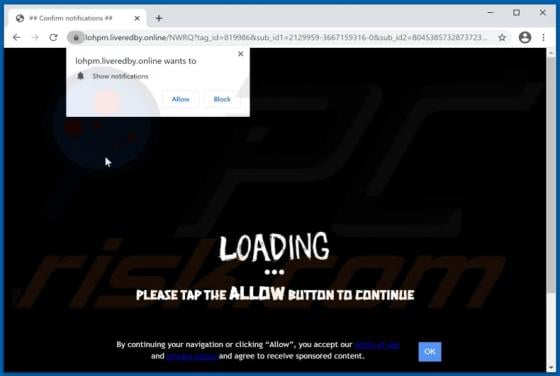
Liveredby.online Ads
Liveredby[.]online can load its deceptive content and open potentially malicious websites. This page is similar to wcoulditbe[.]club, eyourcom[.]fun, ompanied[.]top, and a great number of other pages that serve the same purpose. Usually, pages like liveredby[.]online are promoted through shady ad