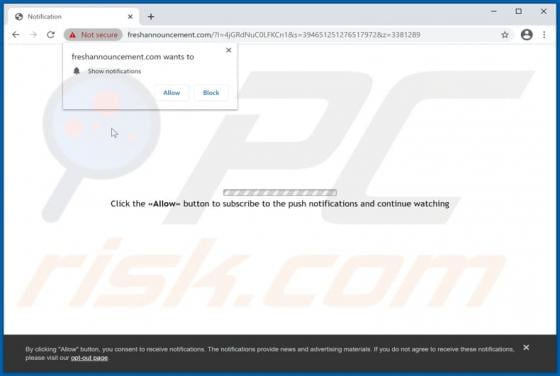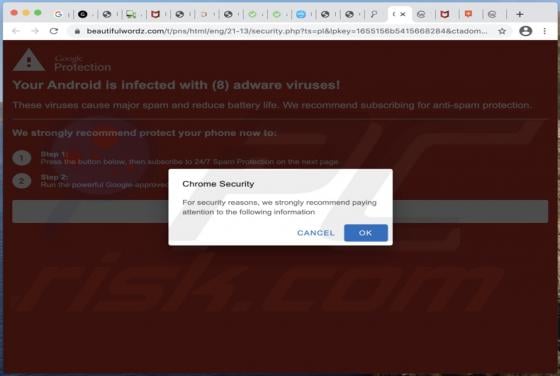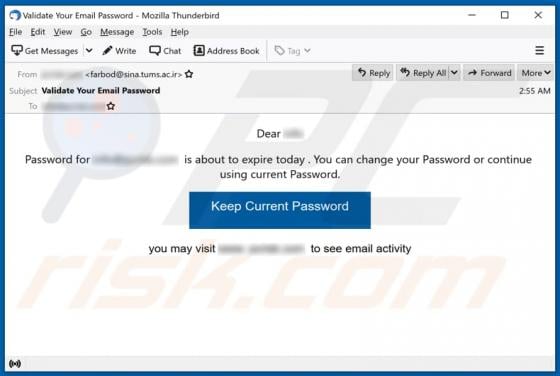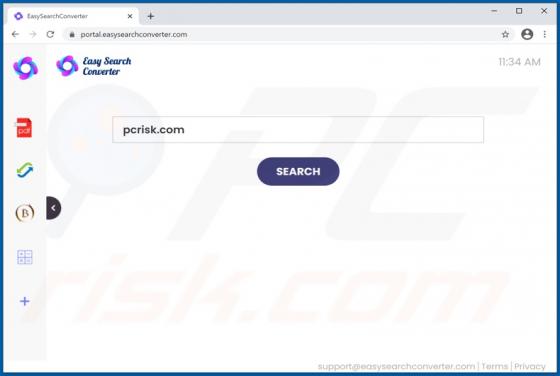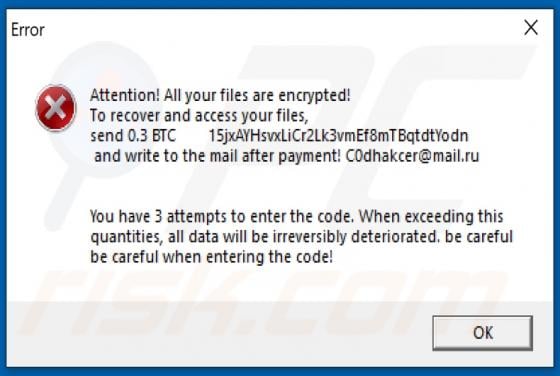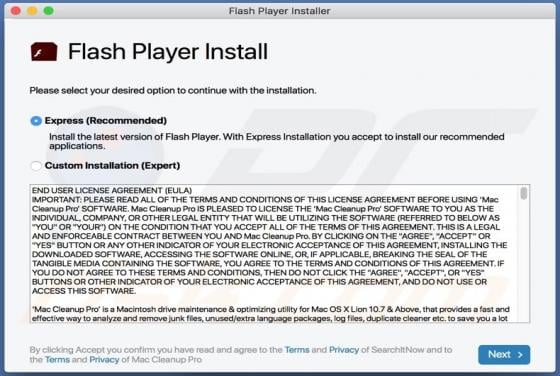
SearchBrowserSky Adware (Mac)
SearchBrowserSky is the name of an application distributed using a fake installer, which appears similar to the installer for Adobe Flash Player. Apps distributed using such methods are often downloaded and installed by users inadvertently and are thus classified as potentially unwanted applicat