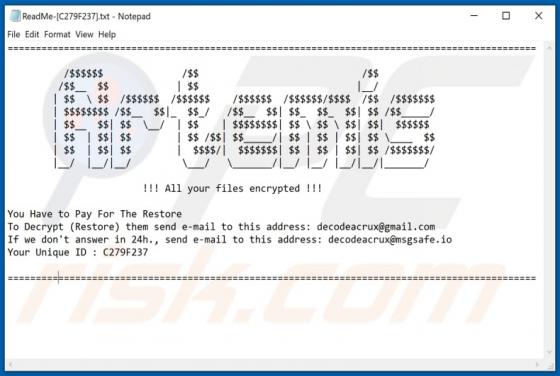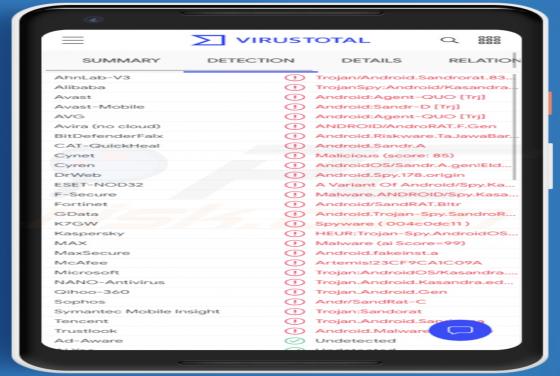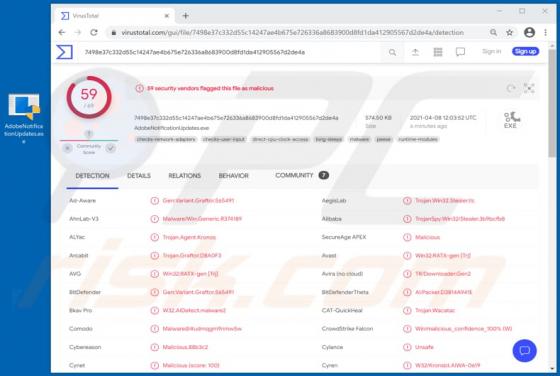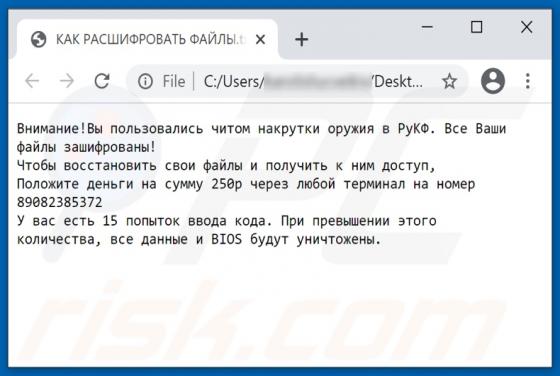
Lmas Ransomware
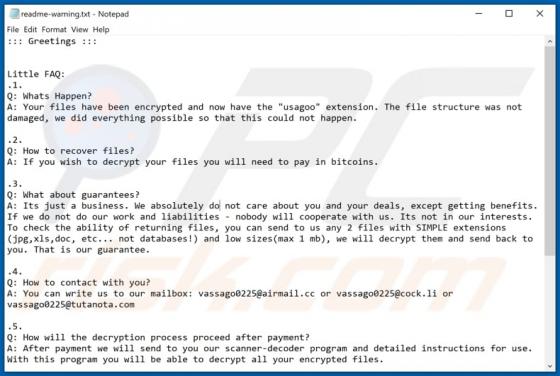
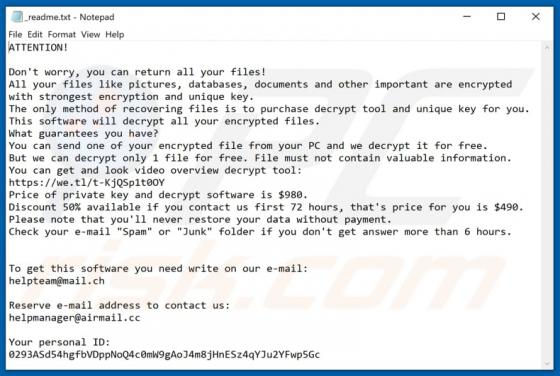
Ransomware is a type of malicious software that makes files inaccessible/unusable by encryption and displays/creates a ransom message. This type of malware of often appends its unique extension to the filenames of all encrypted files. Lmas appends the ".lmas" extension. For example, "1.jpg" is re