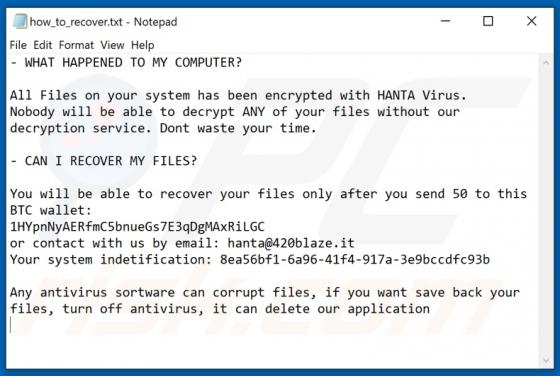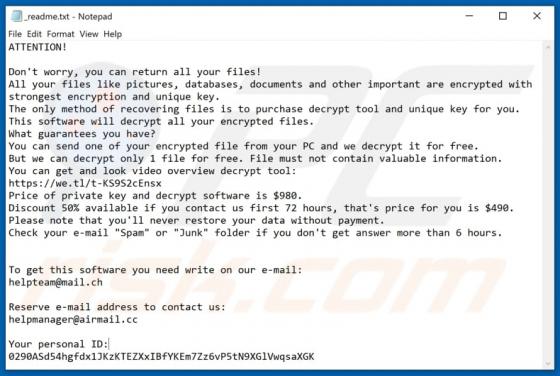
Ytbn Ransomware
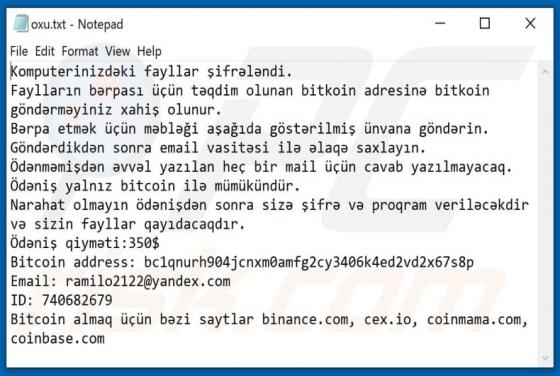
Ransomware is a type of malware that blocks access to data by encryption and keeps it inaccessible unless victims use valid decryption software or keys. Ytbn encrypts files and appends the ".ytbn" extension to filenames. For example, "1.jpg" is renamed to "1.jpg.ytbn", "2.jpg" to "2.jpg.ytbn", an