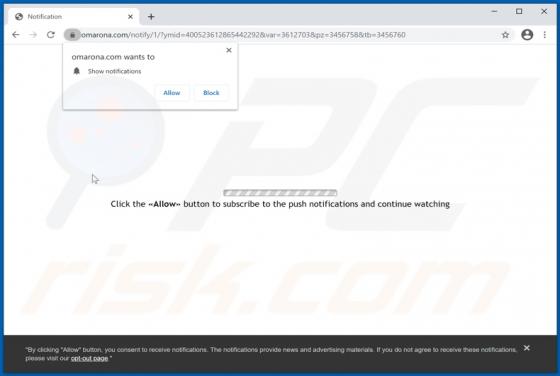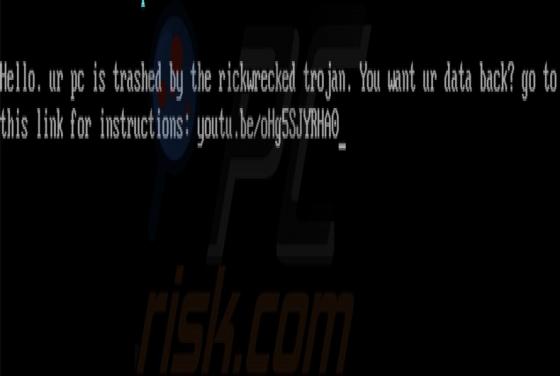
Rickwrecked Ransomware
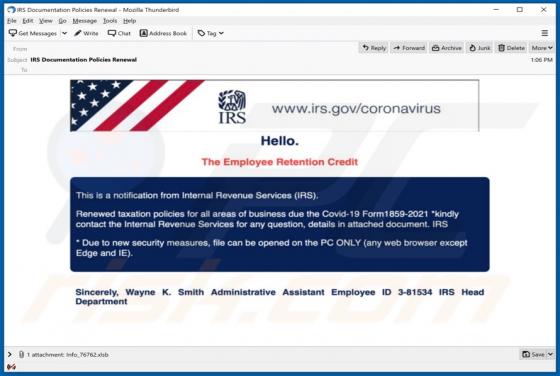
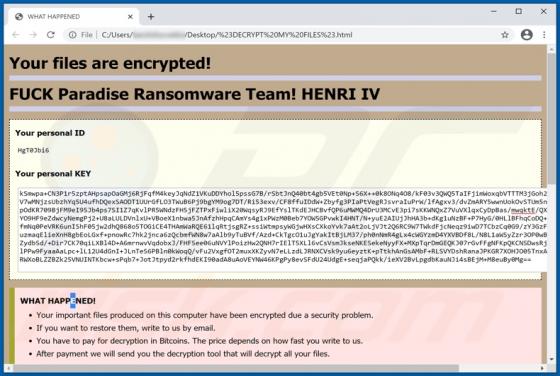
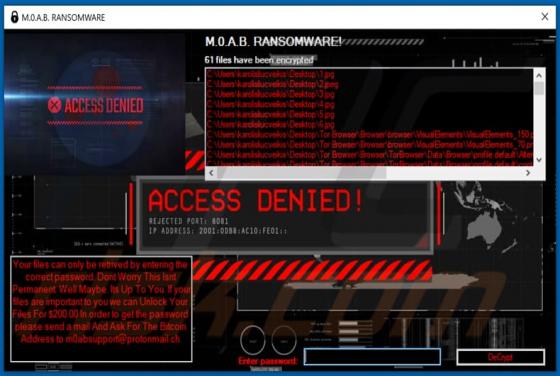
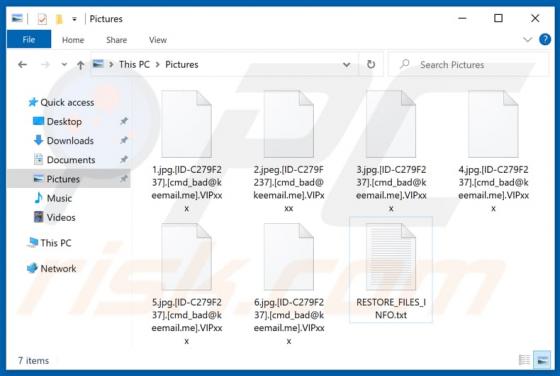
Rickwrecked is a malicious program classified as ransomware with screenlocker traits. Typically, malicious software within this classification encrypts files and/or locks the device screen to make ransom demands. In fact, the purpose of Rickwrecked is not monetary gain, as victims are not presente