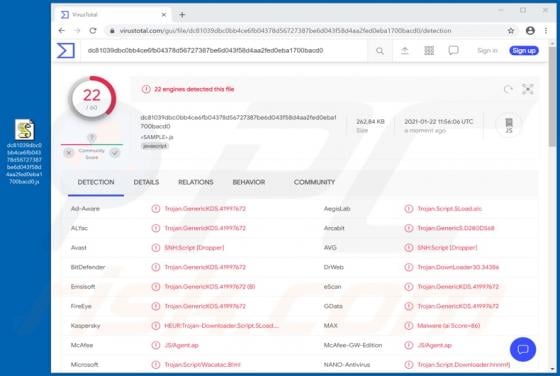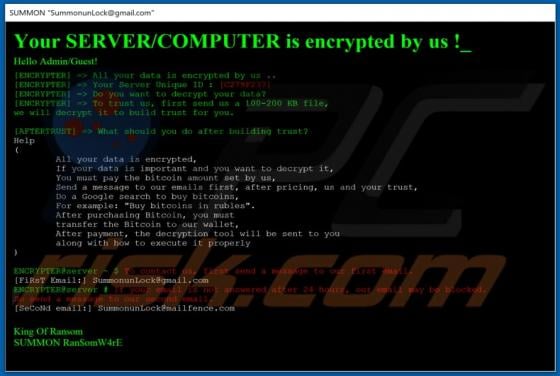
SUMMON Ransomware
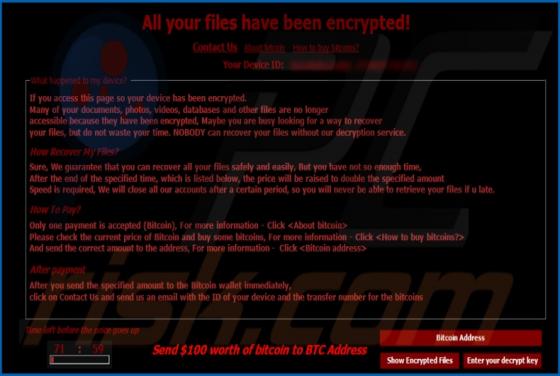
SUMMON encrypts victim's files, renames them, and displays a ransom message ("#ReadThis.HTA"). It renames each encrypted file by prepending the summonunlock@gmail.com email address, victim's ID, and appending the ".SUMMON" extension to the filename. For example, "1.jpg" is renamed to "[SummonunLo