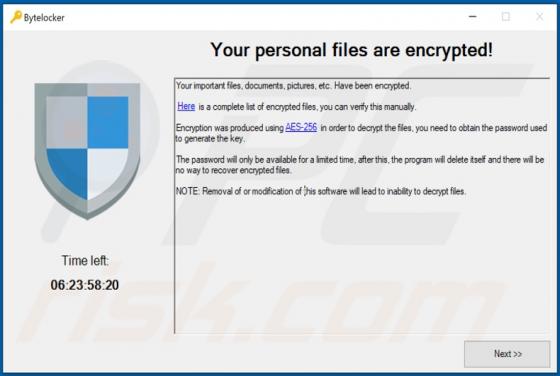
Burofax Online Email Virus
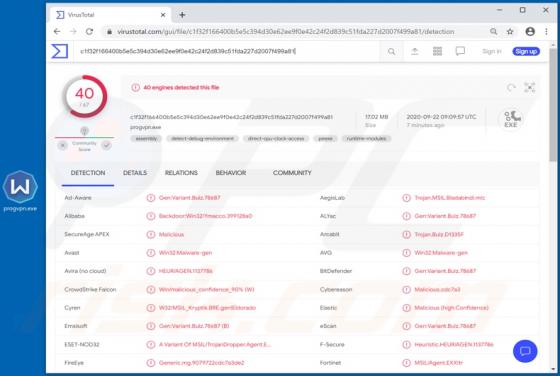
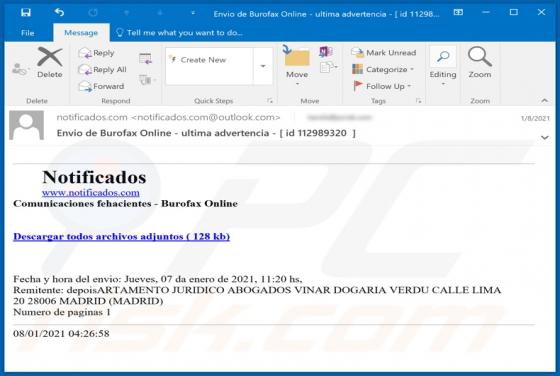
"Burofax Online" refers to a spam email campaign spreading the Mekotio Trojan. The term "spam campaign" describes a large-scale operation, during which thousands of deceptive/scam emails are sent. The messages sent in this particular campaign are disguised as notifications concerning an unspecifi