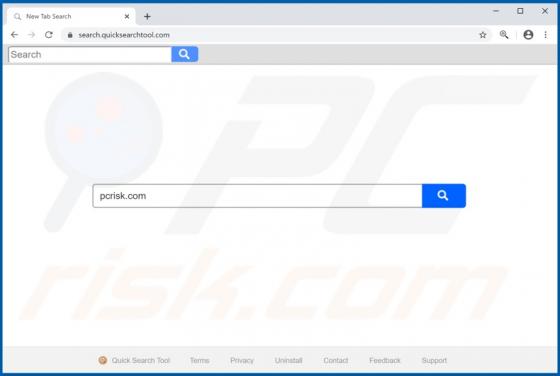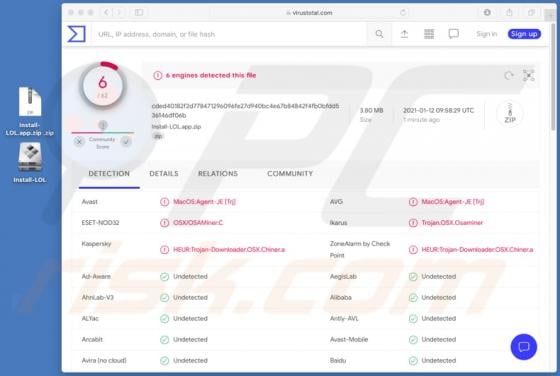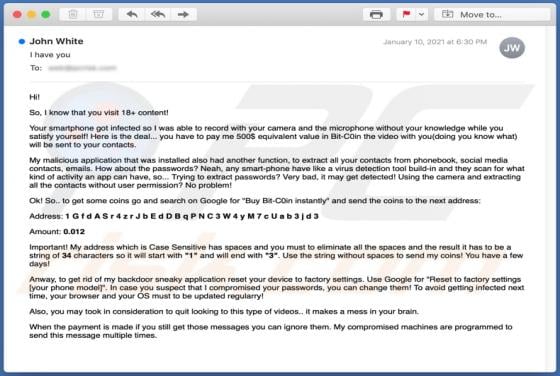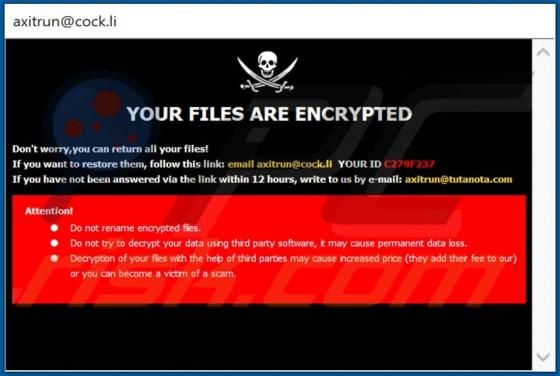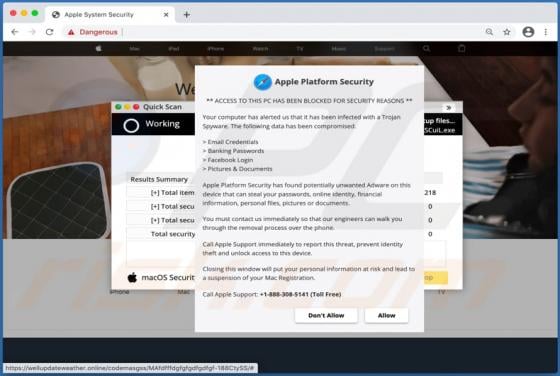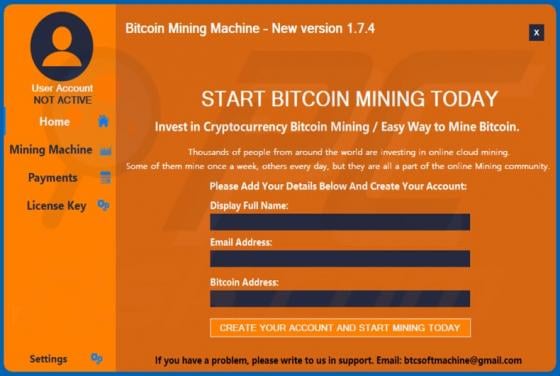
Bitcoin Mining Machine Virus
Bitcoin Mining Machine is a legitimate cryptocurrency miner, however, there is a fake miner with the same name on the internet. Unsuspecting users who download and install the fake miner actually install malicious software called RedLine, an information stealer with the capability to install addit