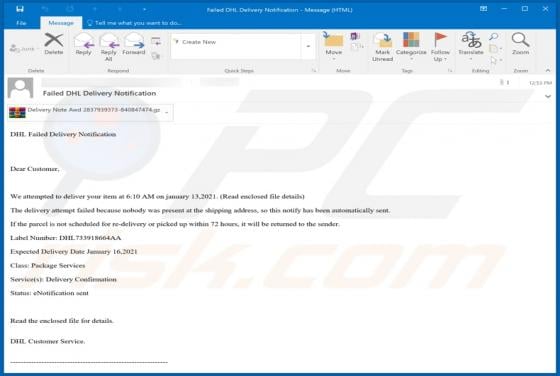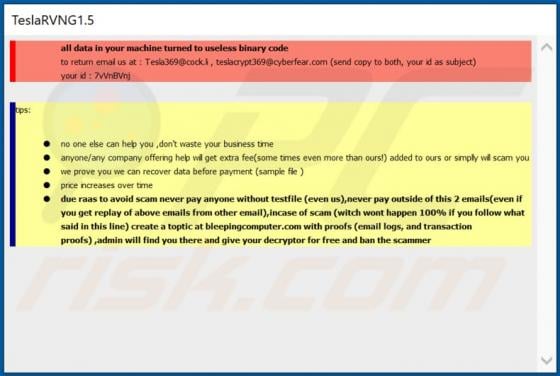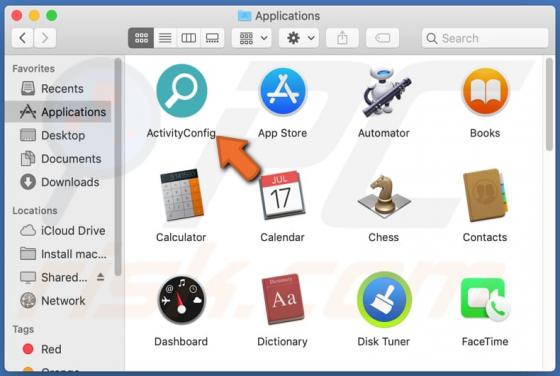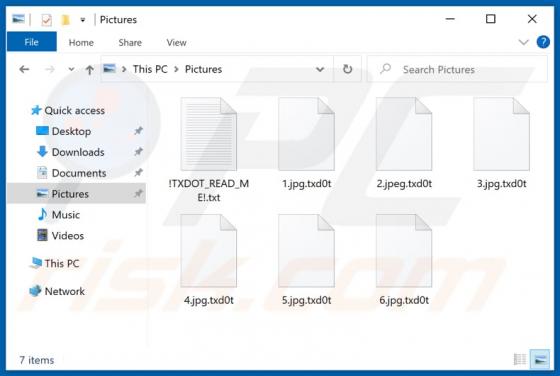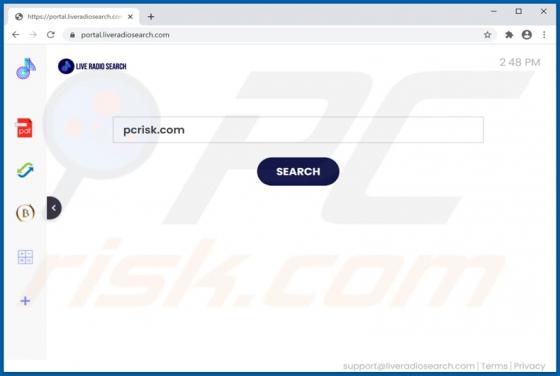
LiveRadioSearch Browser Hijacker
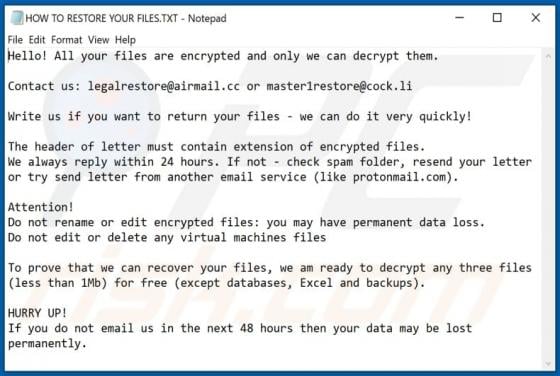
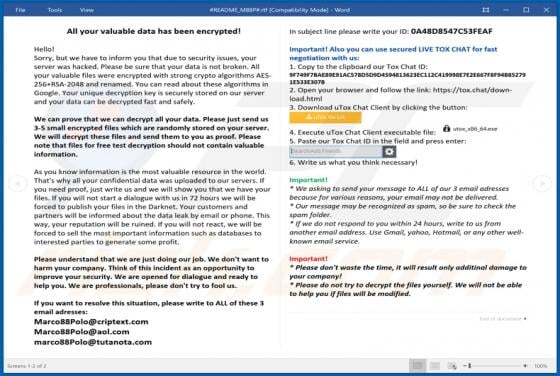
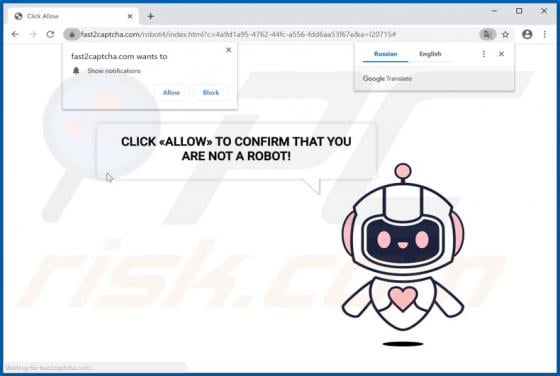
LiveRadioSearch promotes liveradiosearch.com, a fake search engine. Like most apps of this type, LiveRadioSearch achieves this by changing browser settings without users' permission. Furthermore, this app gathers browsing-related data. People often download and install browser hijackers inadvert