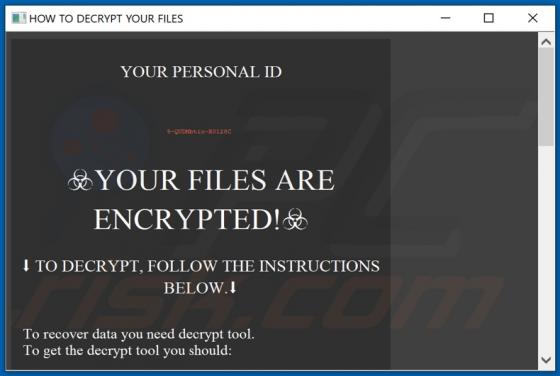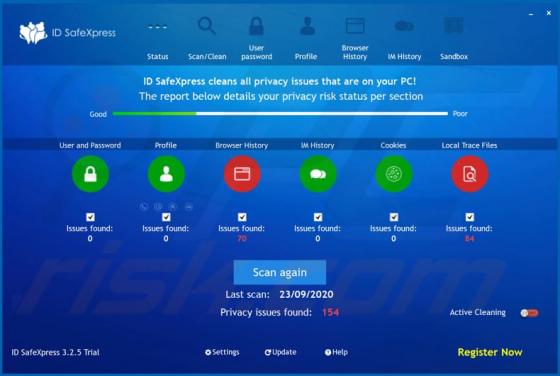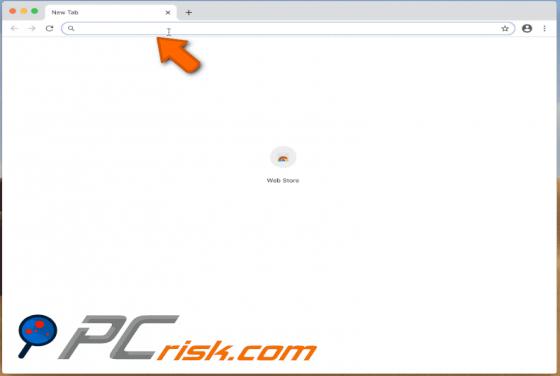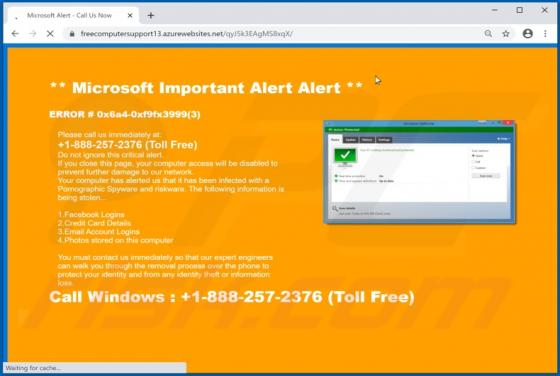
Palnk.pw Ads
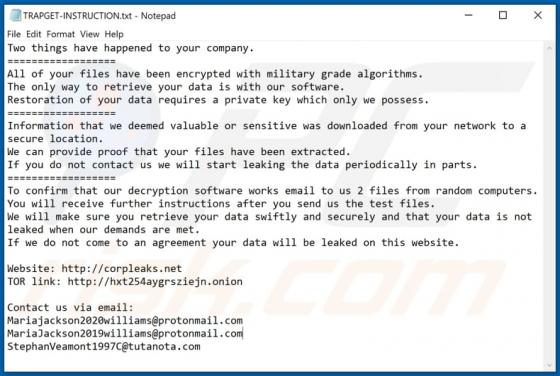
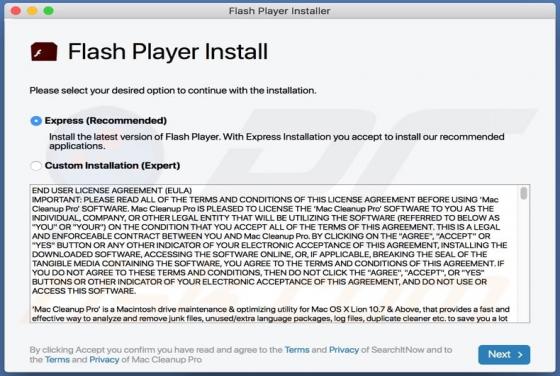
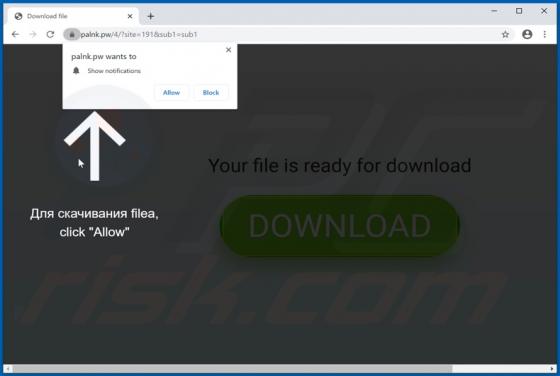
Practically identical to jioer.pro, mybestnewz.com, mypushz.com and thousands of others, palnk[.]pw is a rogue site. Visitors to this web page are presented with dubious material and/or are redirected to other untrusted or possibly malicious websites. Most users do not enter palnk[.]pw intentiona