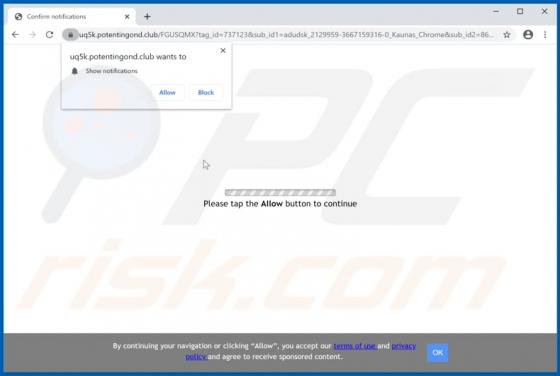
Mac Optimizer Pro Unwanted Application (Mac)
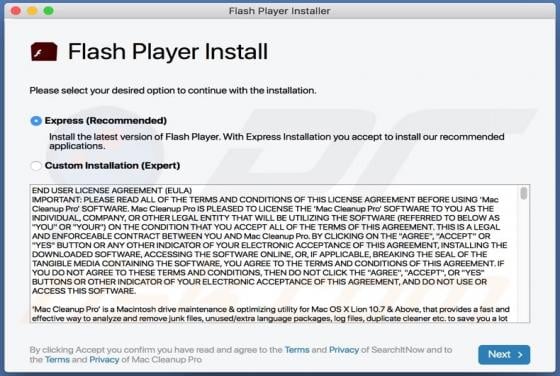
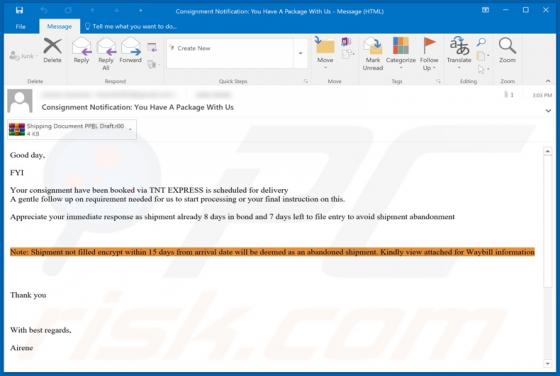
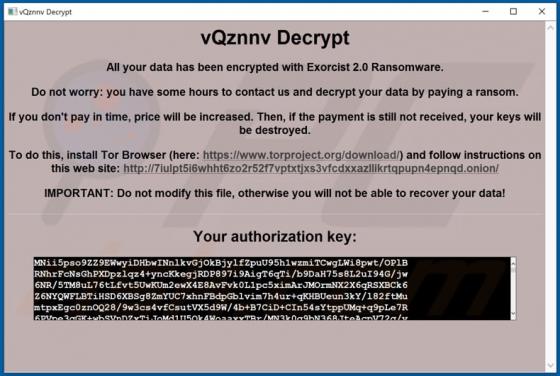
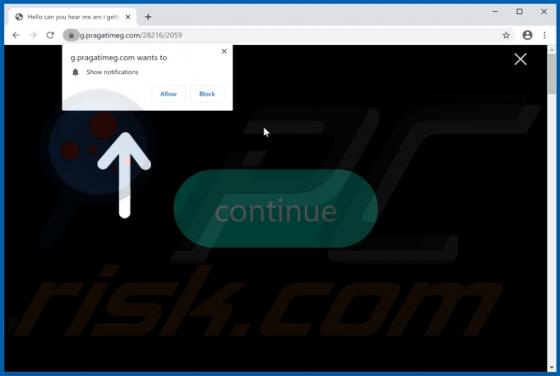
Mac Optimizer Pro is promoted as software for cleaning and optimizing Mac Operating Systems, however, due to the dubious techniques used to proliferate this app, it is classified as a Potentially Unwanted Application (PUA). Software within this classification may be nonoperational and/or have un