Ijikpvj Ransomware
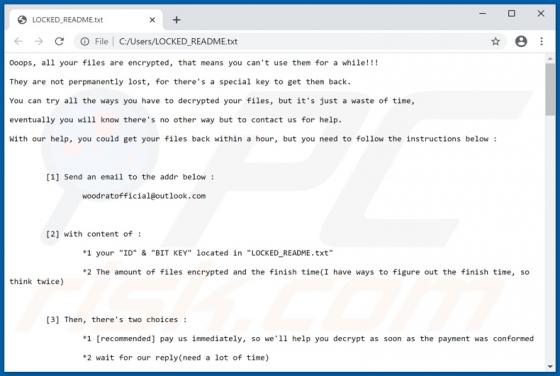
Ijikpvj ransomware encrypts files, renames them and creates a ransom message. It renames files by appending its extension (".ijikpvj") to filenames. For example, "1.jpg" is renamed to "1.jpg.ijikpvj", "2.jpg" to "2.jpg.ijikpvj", and so on. Ijikpvj also creates the "HOW TO RESTORE YOUR FILES.TXT"