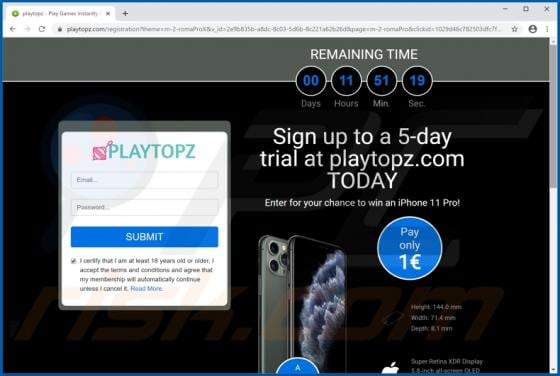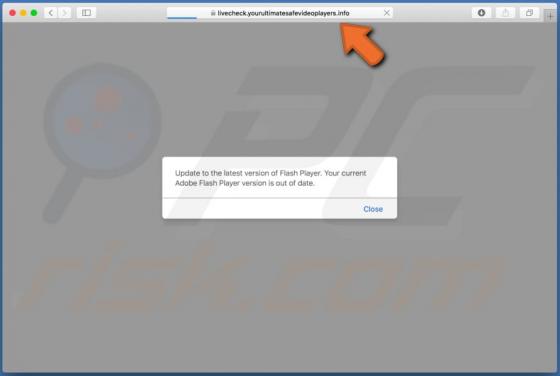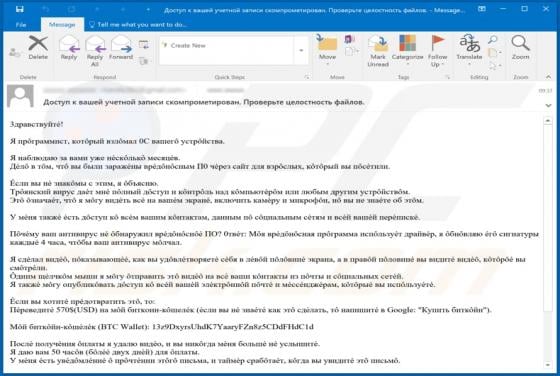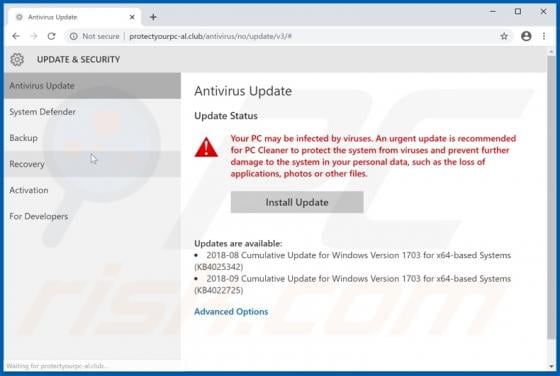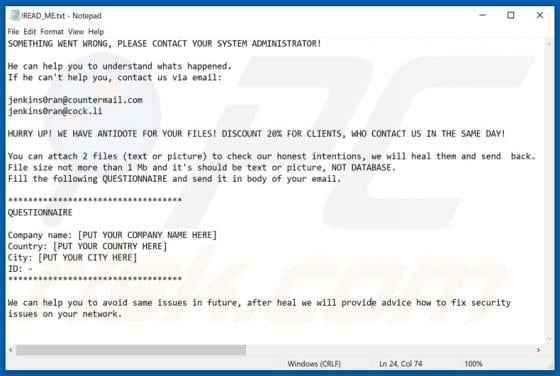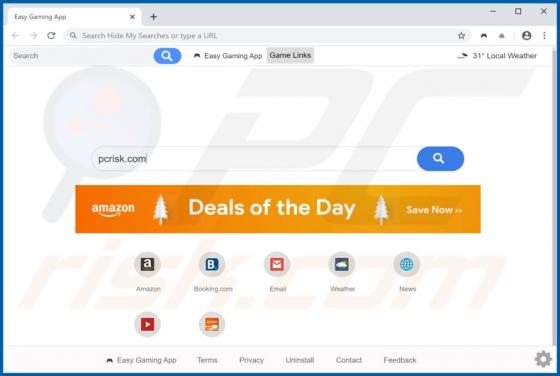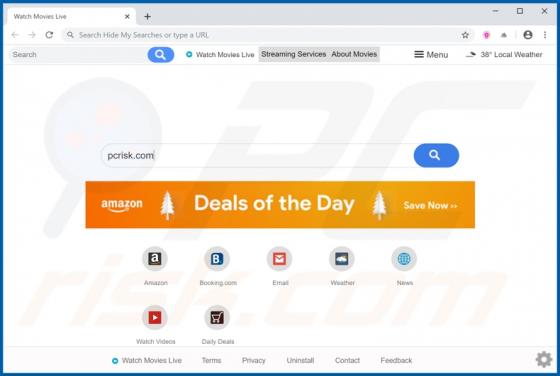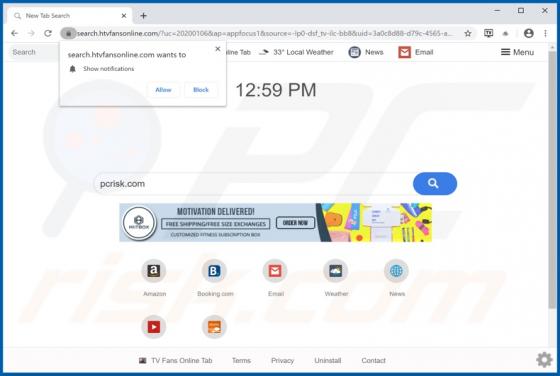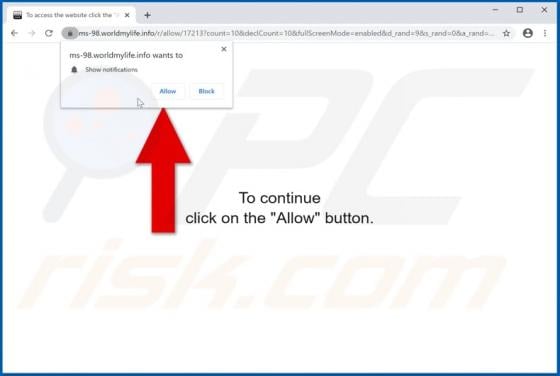
Worldmylife.info Ads
worldmylife[.]info is one of many websites (similar to balanceformoon[.]com, mediazone[.]mobi, toobotnews[.]biz and so on) that redirect visitors to other untrustworthy sites or load dubious content. Generally, people do not visit these websites intentionally - browsers open them when potentially