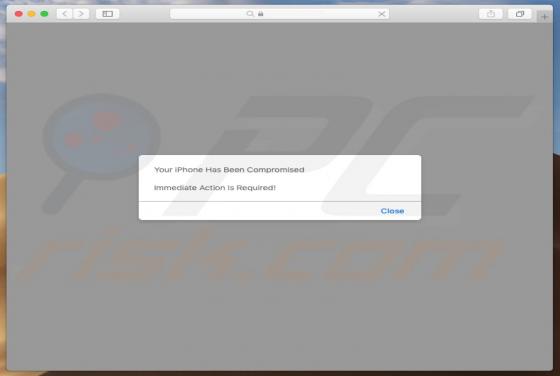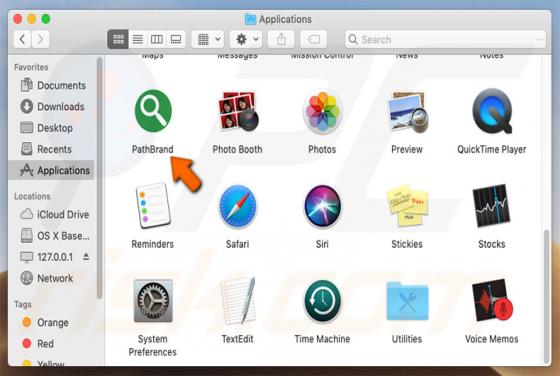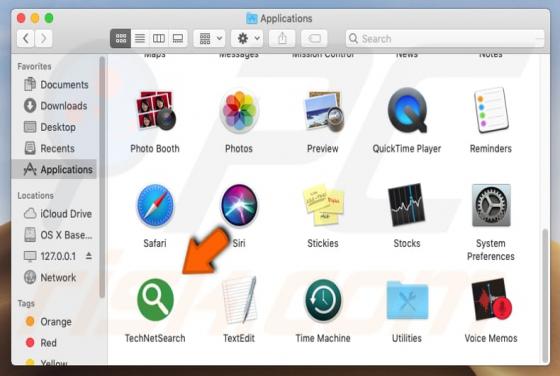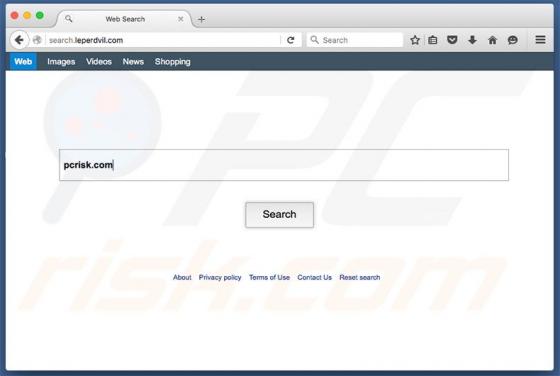
Search.leperdvil.com Redirect (Mac)
Search.leperdvil.com is presented as a legitimate Internet search website similar to Google, Bing, Yahoo, and other legitimate search engines. Some users may believe that search.leperdvil.com is a legitimate site, however, this site is promoted using deceptive app 'installers' developed to modi