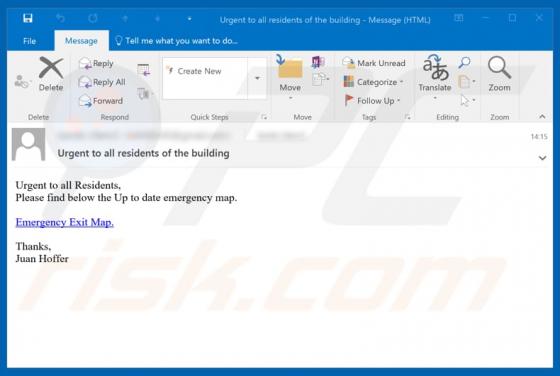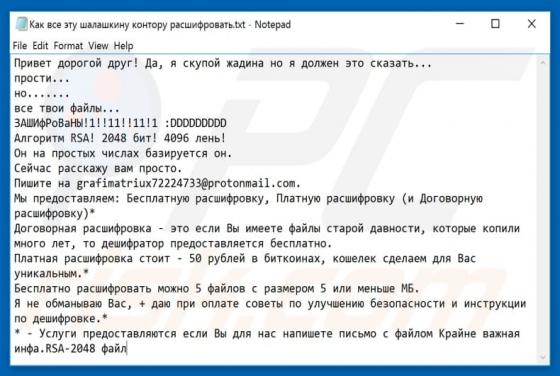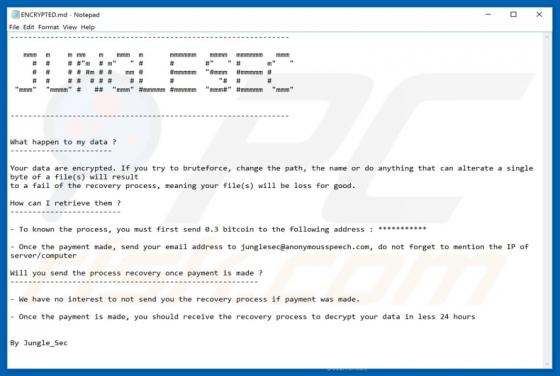
JungleSec Ransomware
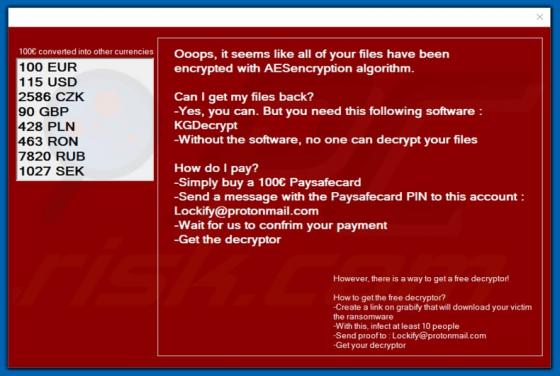
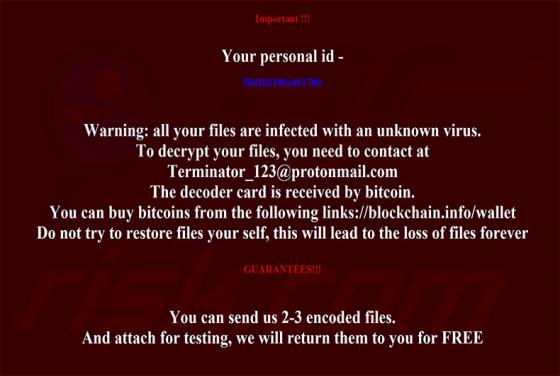
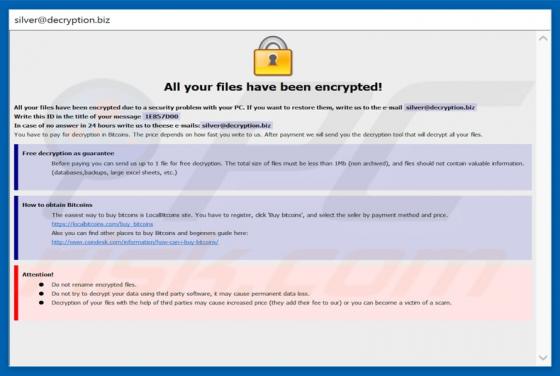
JungleSec is a ransomware-type computer infection that targets mostly Linux servers. In some cases, however, it also infiltrates Windows/Mac servers. Like most viruses of this type, it is designed to encrypt data. To retrieve (decrypt) their files, victims are encouraged to pay developers a ransom