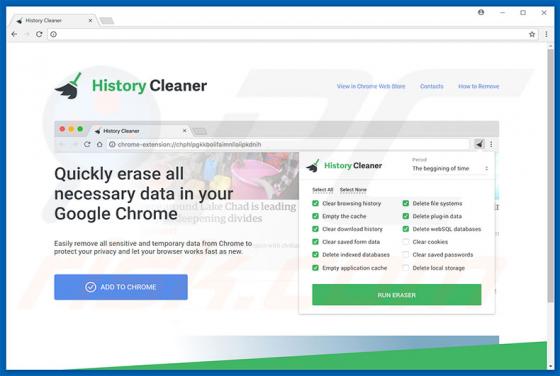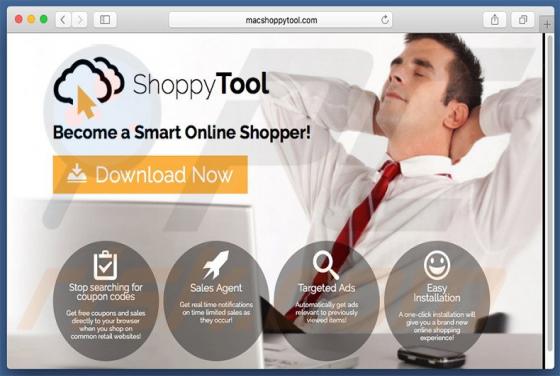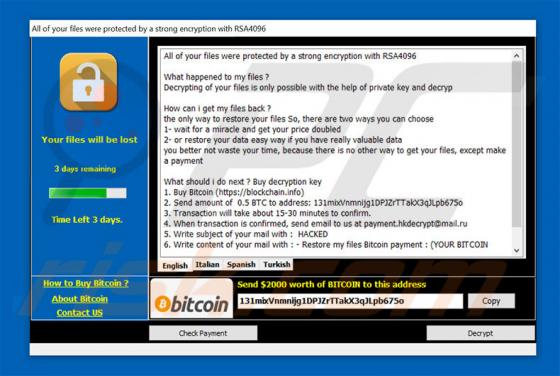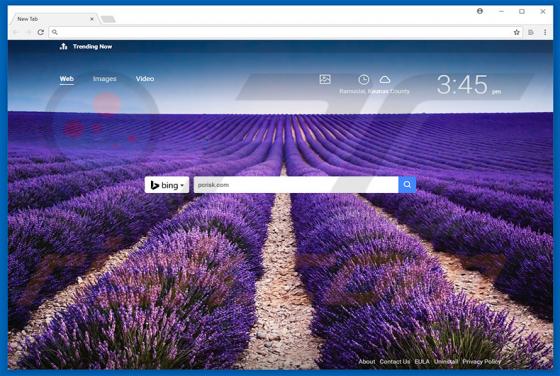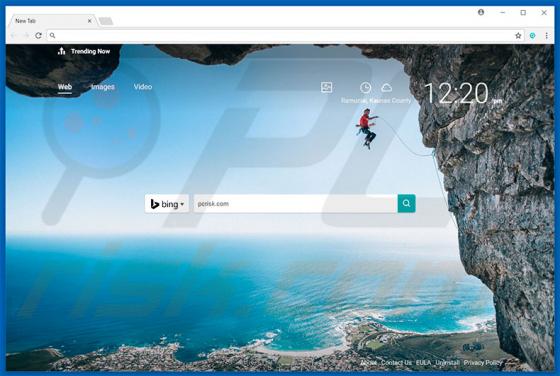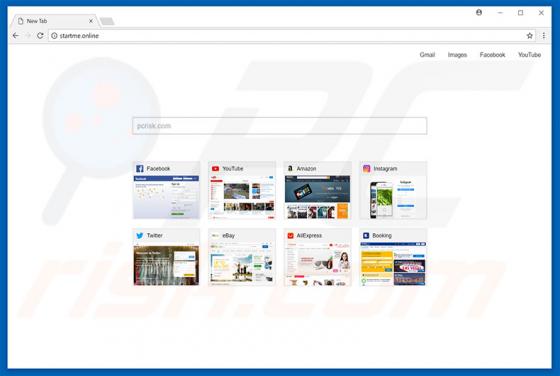
Startme.online Redirect
Identical to launchpage.org, startme.online is a fake Internet search engine that falsely claims to generate improved results, thereby enhancing the browsing experience. These claims often trick users into believing that startme.online is legitimate and useful, however, this website is promoted u