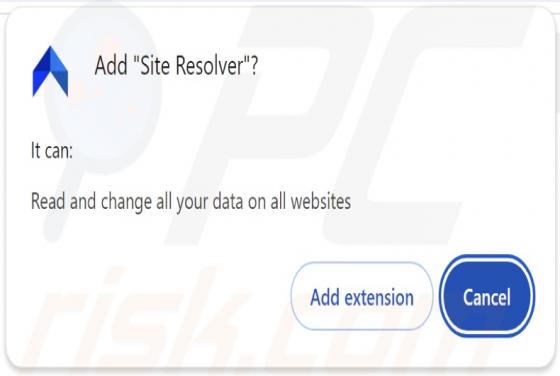
Site Resolver Adware
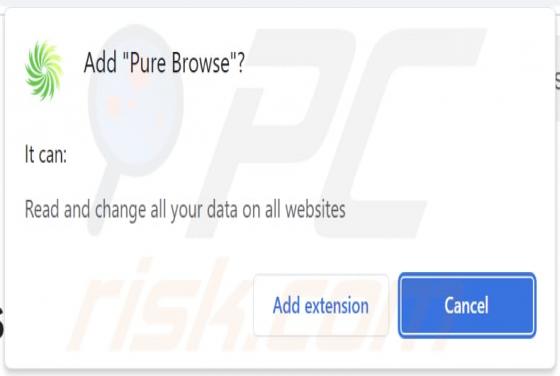
While investigating deceptive websites, our researchers discovered the Site Resolver browser extension. After examining this piece of software, we determined that it operates as adware. Site Resolver runs intrusive advertisement campaigns and spies on users' browsing activity. Adware stand