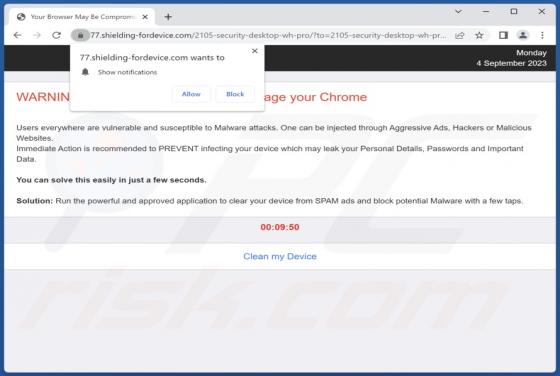
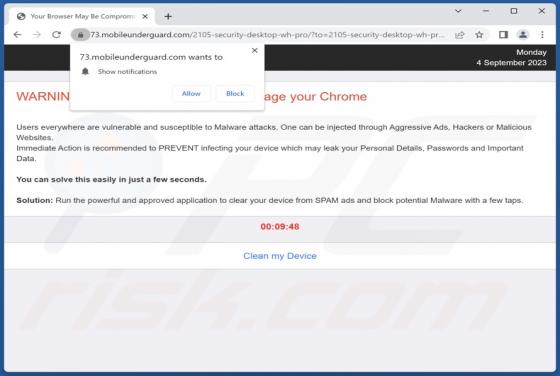
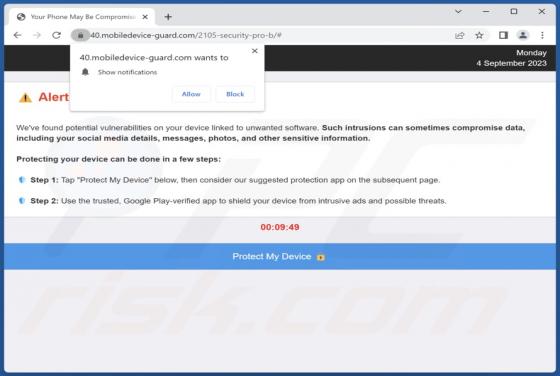
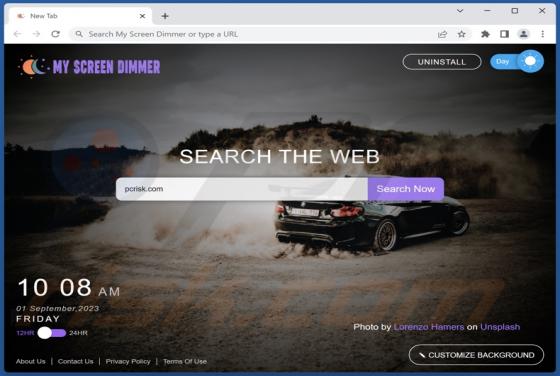
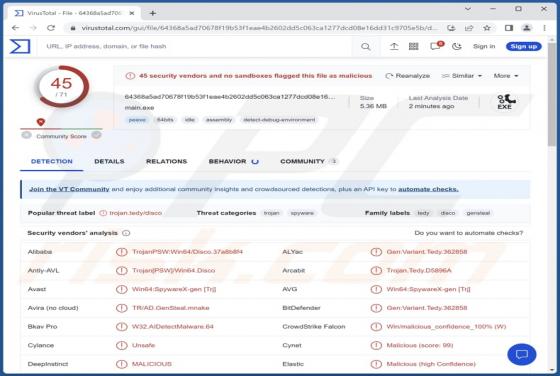
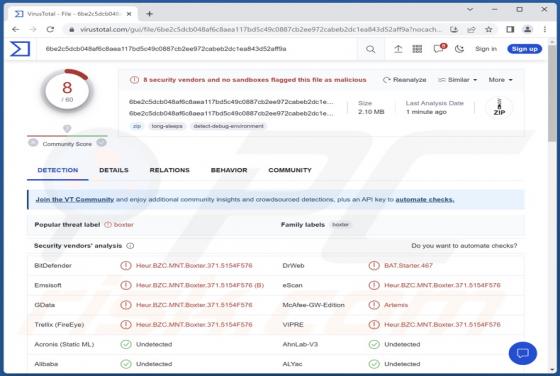
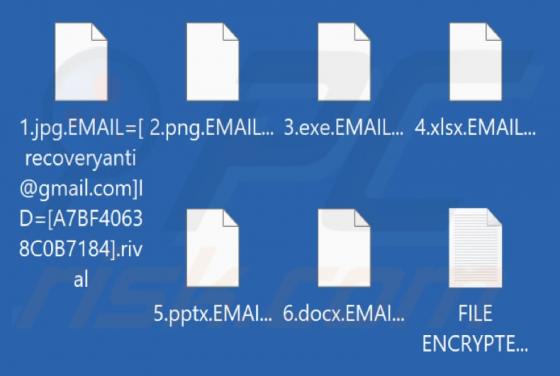
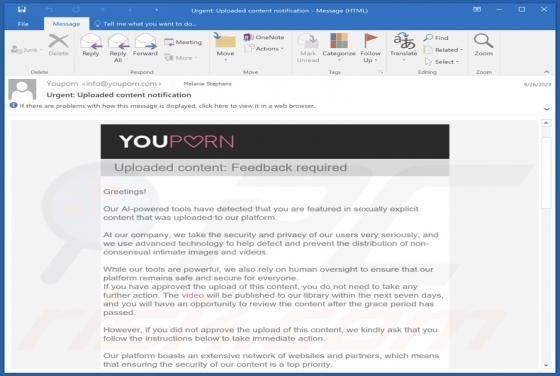
GallusGallus Malicious Extension
During our examination of the GallusGallus browser extension, we uncovered concerning actions such as enabling the "Managed by your organization" functionality in Chrome browsers, controlling specific browser components, and gathering data. Our interaction with GallusGallus took place while invest