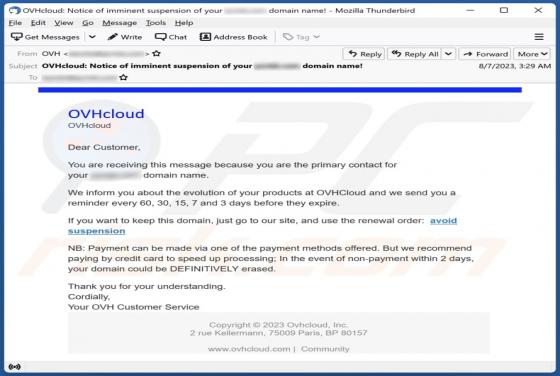
OVHCloud Suspension Email Scam
While investigating this email, our team identified it as a clever phishing attempt disguised as a notice from a cloud service provider. Scammers use this tactic to entice unsuspecting recipients to access a phishing page and submit their personal information. As a result, recipients are advised t