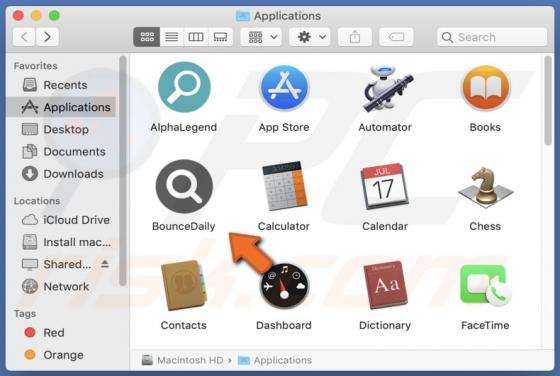
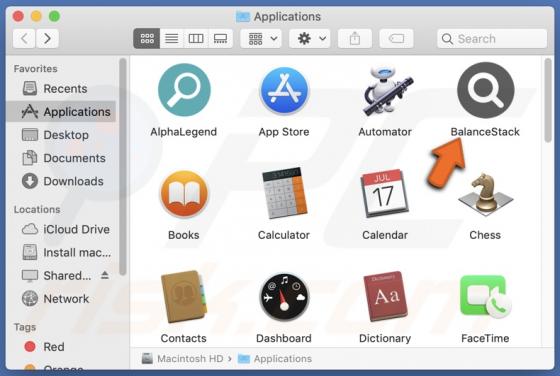
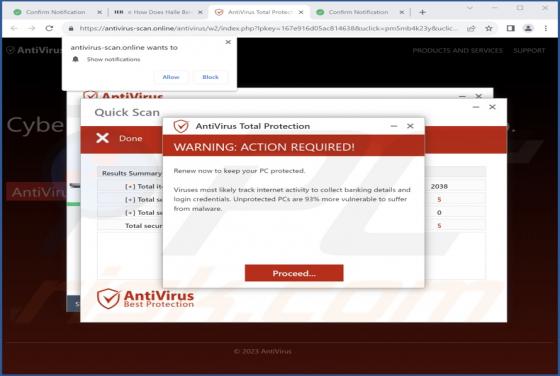
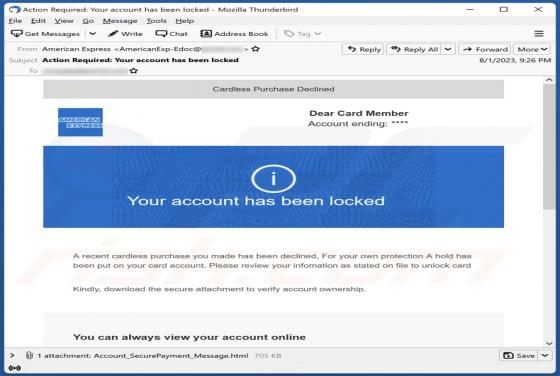
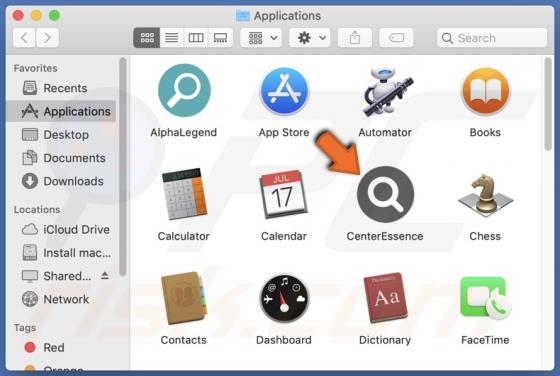
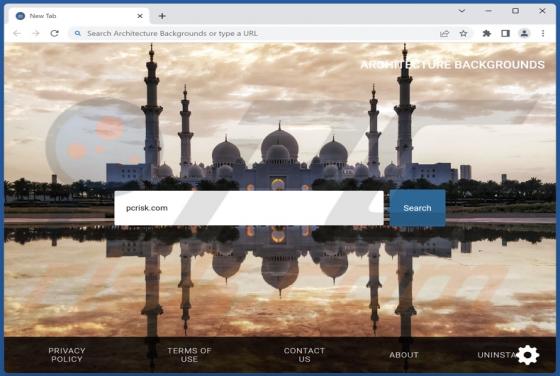
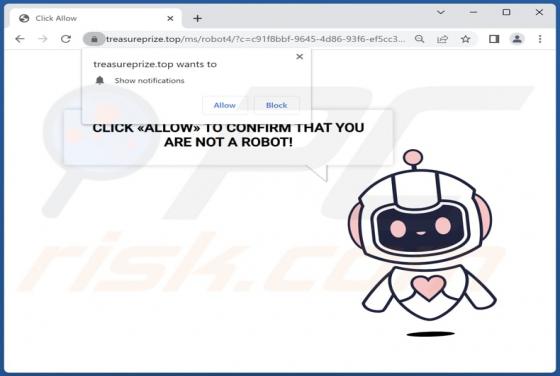
UrbanClassic Adware (Mac)
After investigating UrbanClassic, our team has determined that its primary objective is to display intrusive advertisements to users, categorizing it as adware. It is crucial to highlight that users often download and install applications like UrbanClassic inadvertently due to the distribution m