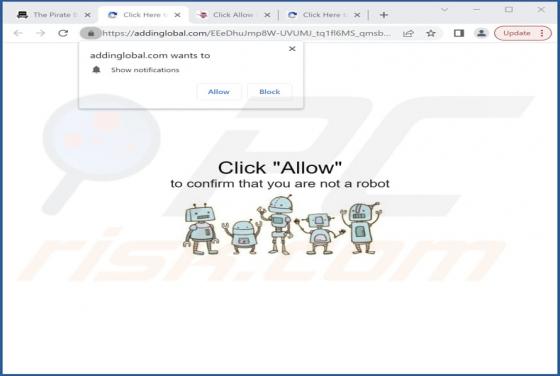
Addinglobal.com Ads
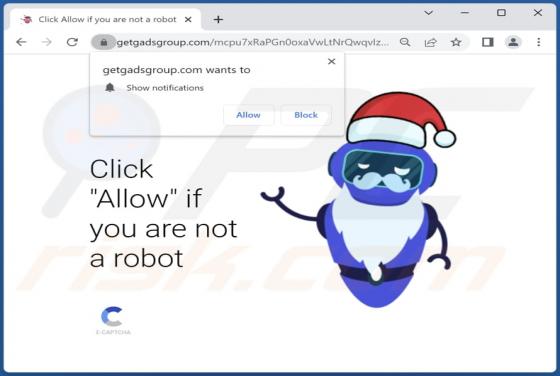
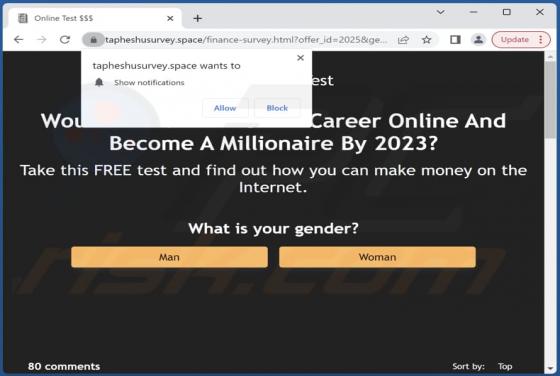
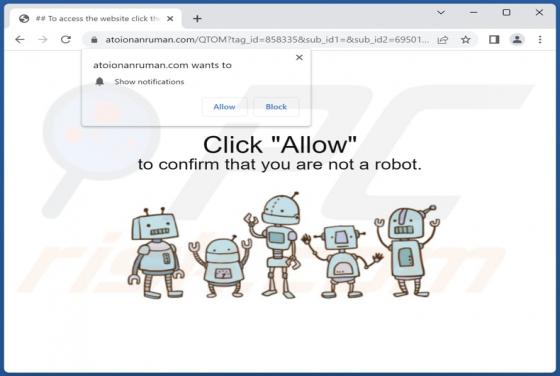
During our investigation of addinglobal[.]com, we discovered that it is among the websites created to deceive visitors into consenting to receive notifications. These notifications can be bothersome and invasive, and in some cases, they may even carry malicious content. Typically, users open sites