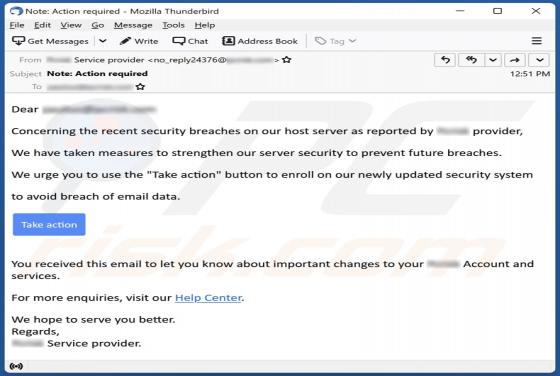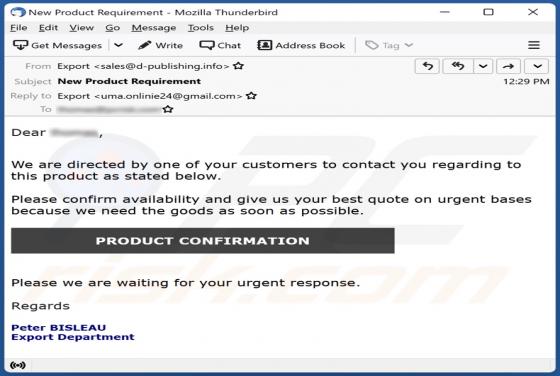
Product Availability Confirmation Email Scam
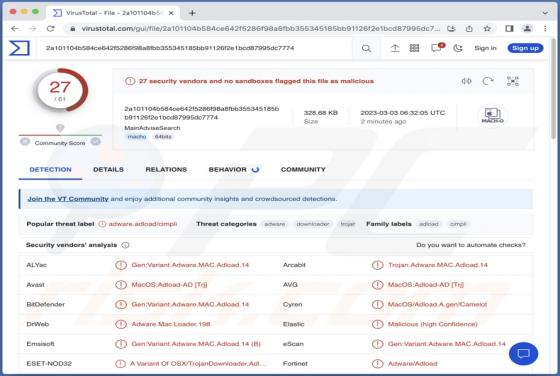
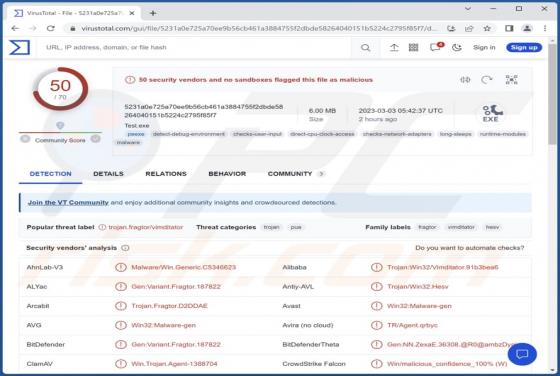
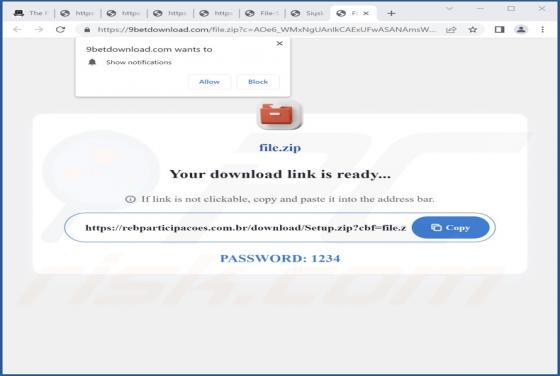
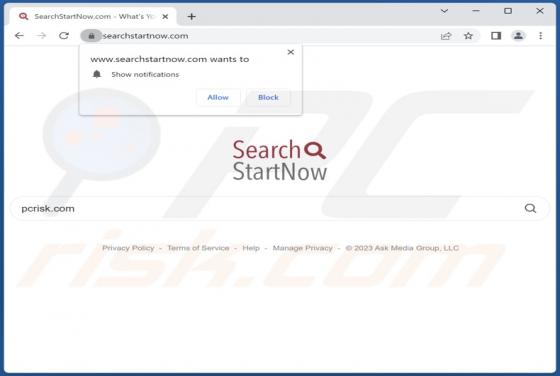
After inspecting the "Product Availability Confirmation" email, we learned that it is spam. The fake letter is presented as an urgent purchase request from the sender. This mail operates as a phishing scam and promotes a phishing site disguised as SharePoint. This website is designed to record and