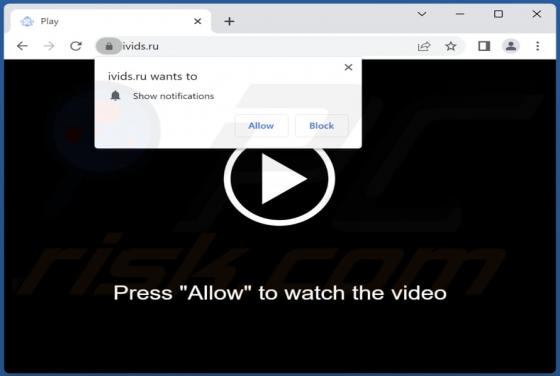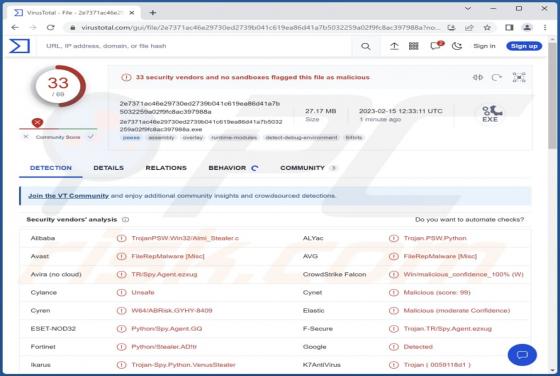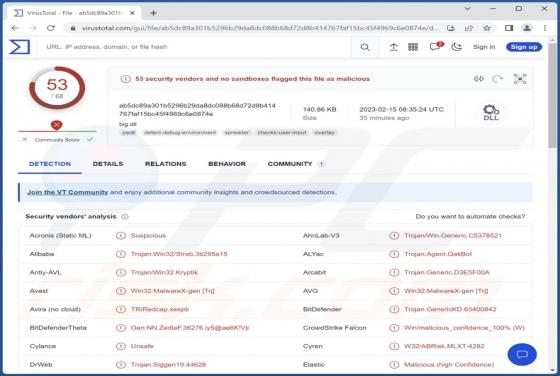
Inghesatin.com Ads
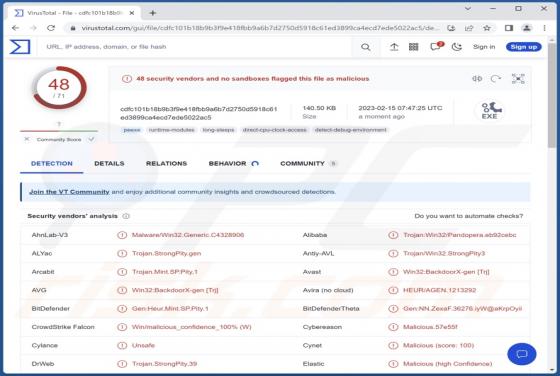
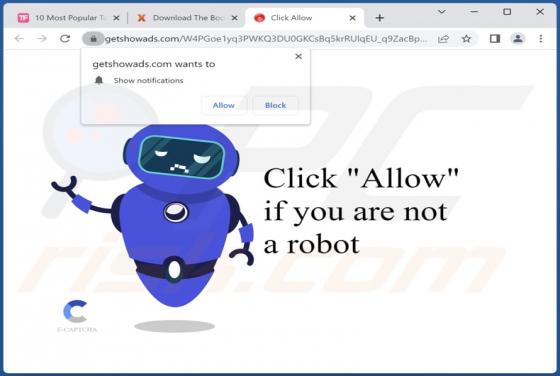
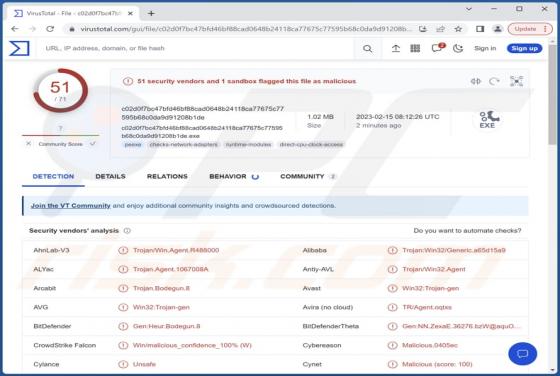
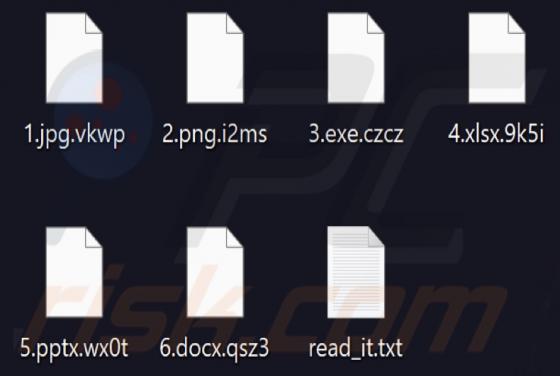
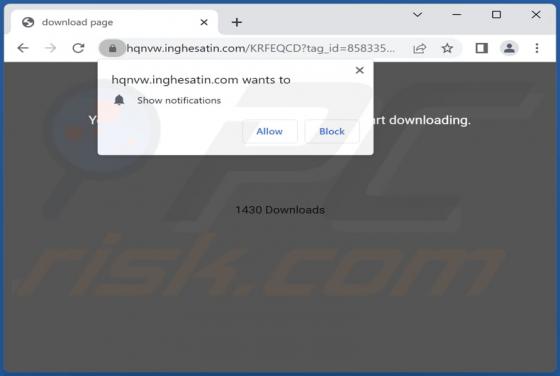
Our team has investigated inghesatin[.]com and found that the purpose of this page is to lure visitors into agreeing to receive notifications. Inghesatin[.]com displays deceptive content to convince visitors to allow it to show notifications. Also, inghesatin[.]com redirects to similar websites.