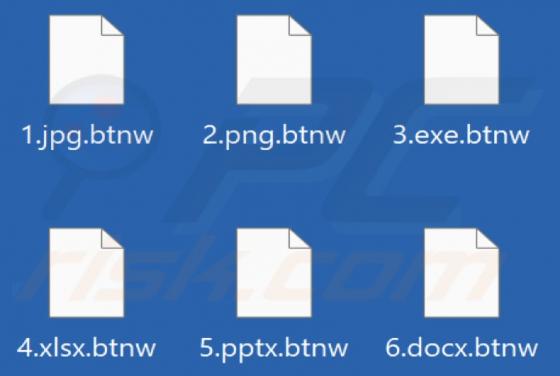
Btnw Ransomware
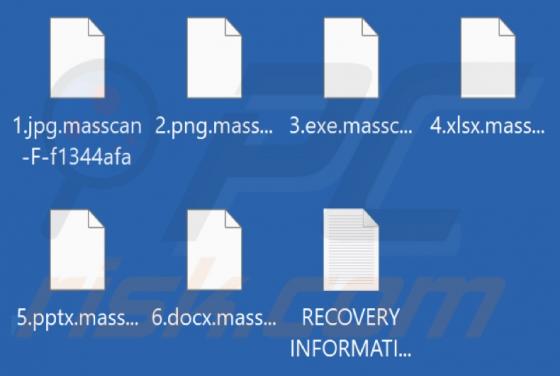
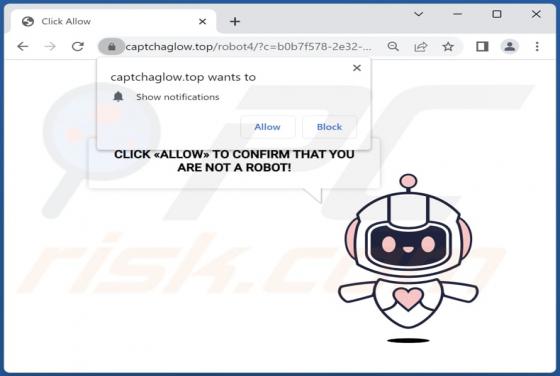
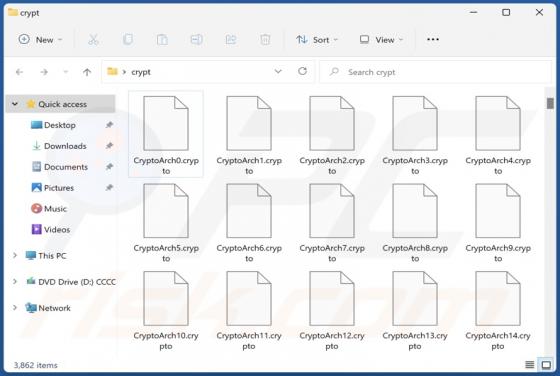
Btnw is the name of ransomware that our team has discovered while analyzing malware samples submitted to VirusTotal. We found that Btnw belongs to a ransomware family called Djvu. Ransomware variants belonging to this family are often distributed alongside information stealers such as RedLine and