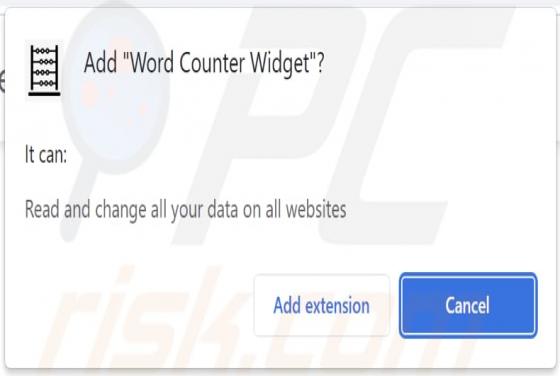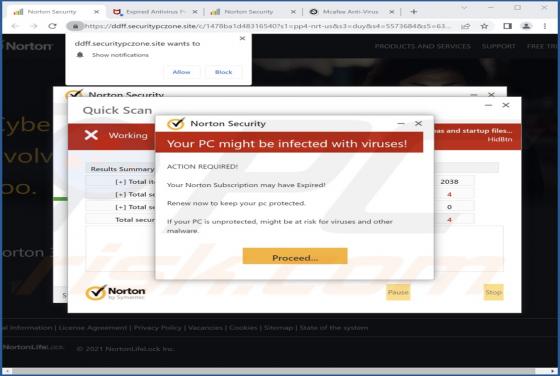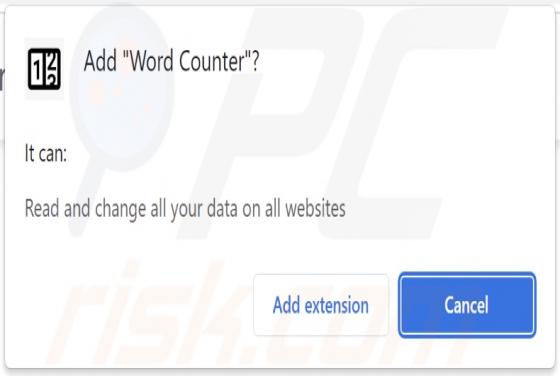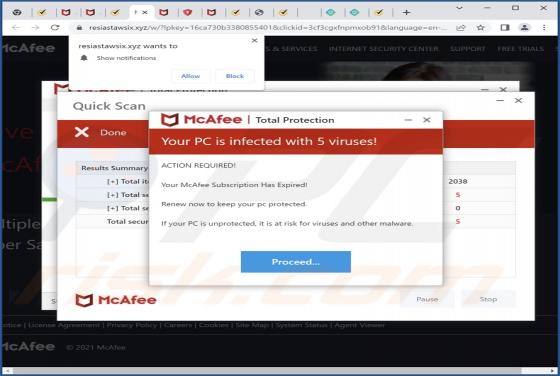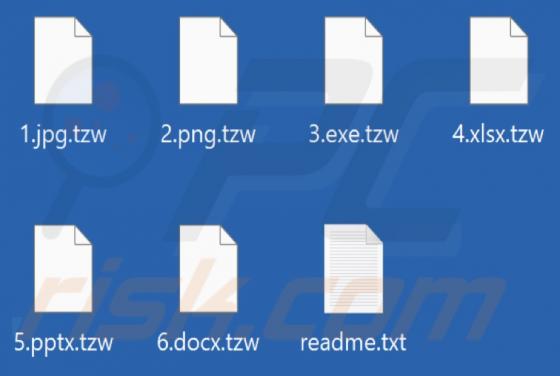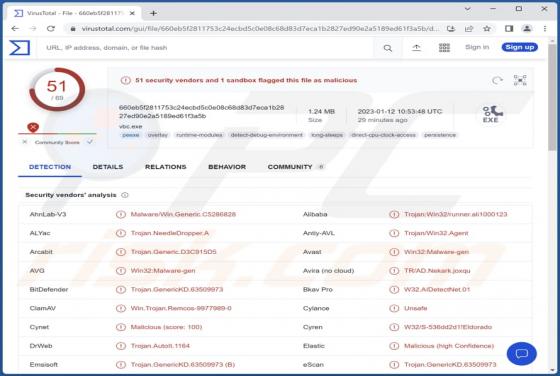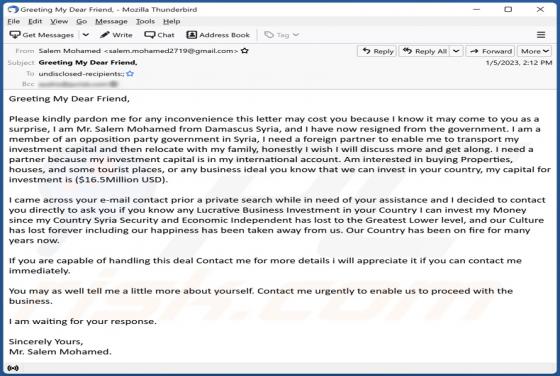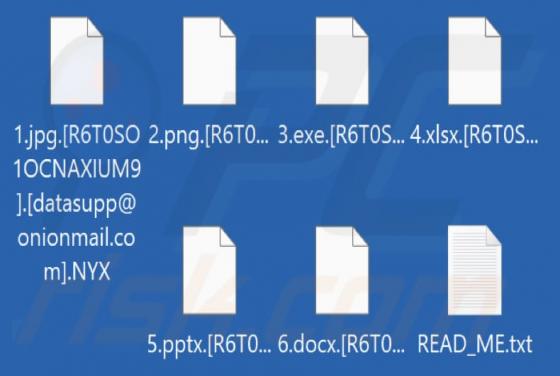
Yourtopleveldefence.site Ads
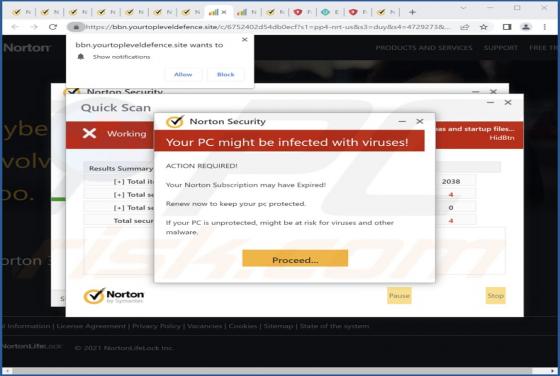
Our team has analyzed yourtopleveldefence[.]site and learned that the purpose of this site is to trick visitors into purchasing antivirus software. However, yourtopleveldefence[.]site uses a scare tactic to promote that software - it displays a fake virus warning. Typically, users open such pages