Cats Fanpage Browser Hijacker
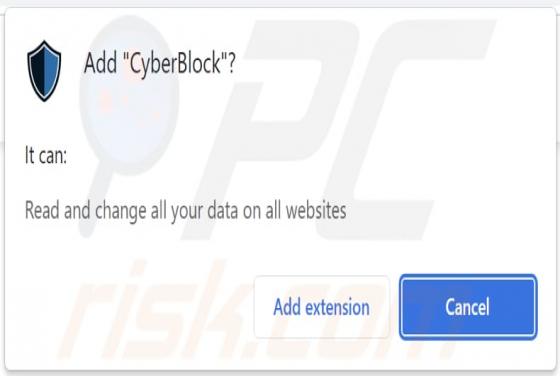
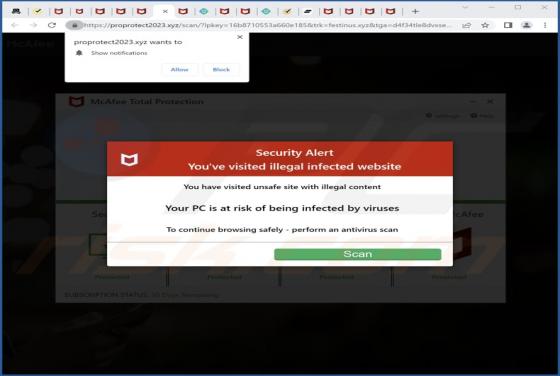
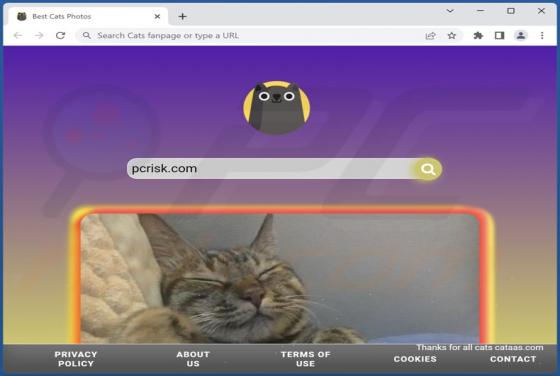
After testing the Cats fanpage browser extension, we found that it is a browser hijacker designed to promote search.cats-fan.com - a fake search engine. Cats fanpage hijacks a web browser by changing some of its settings. Usually, browser hijackers are promoted in deceptive ways. Cats fanp