Cophypserous.com Ads
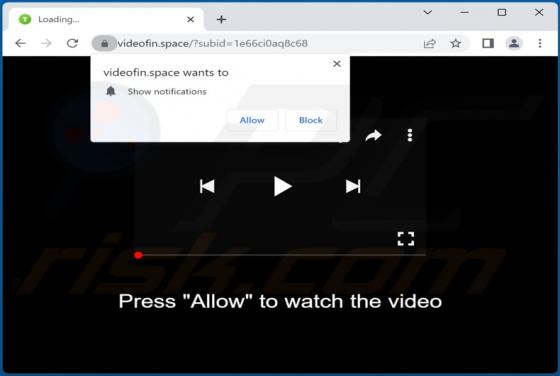
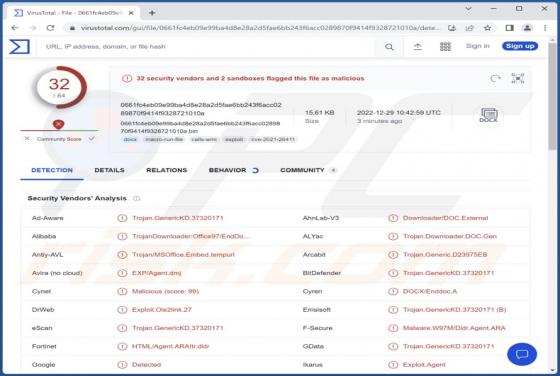
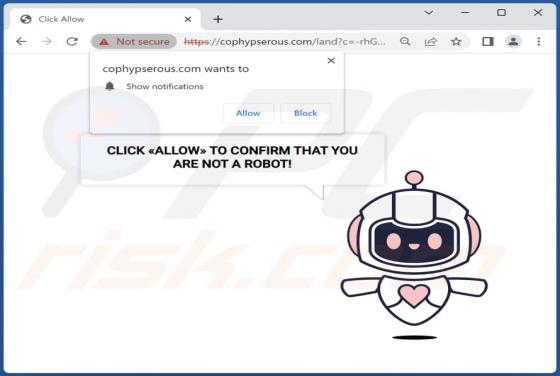
While analyzing cophypserous[.]com, we found that it is an untrustworthy web page that shows a deceptive message to lure visitors into allowing it to show notifications. Our team discovered cophypserous[.]com while inspecting websites that use shady advertising networks. Cophypserous[.]com