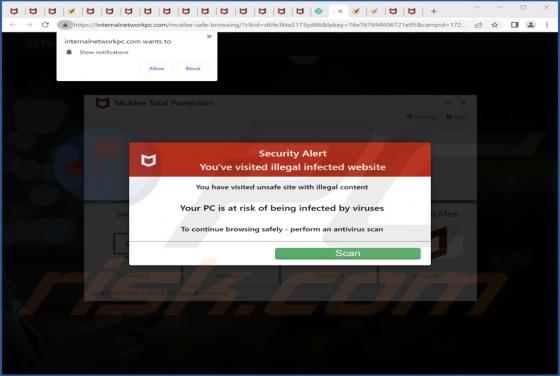
Internalnetworkpc.com Ads
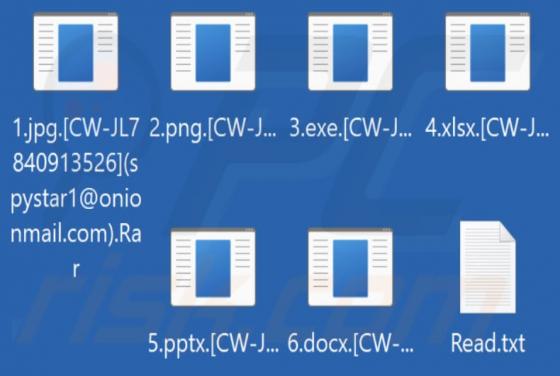
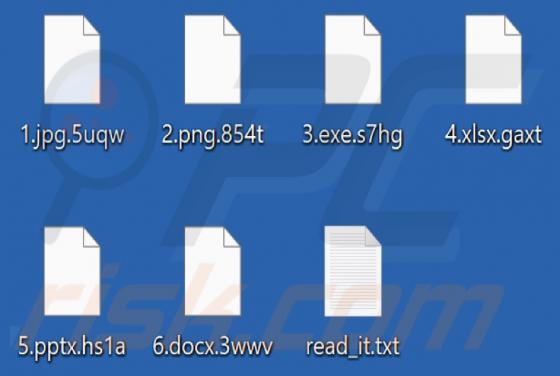
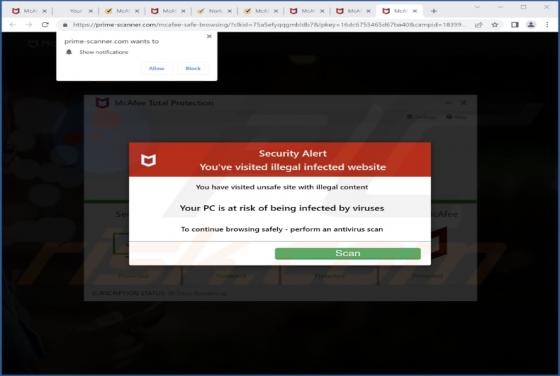
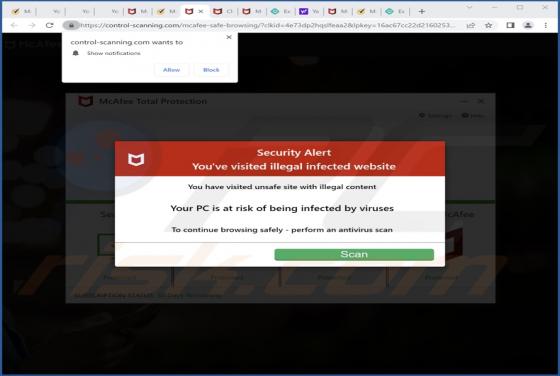
Internalnetworkpc[.]com is a rogue page that our researchers discovered while inspecting dubious websites. The site in question promotes online scams and spam browser notifications. It is also capable of redirecting users to other (likely unreliable/dangerous) webpages. Sites like internalnetwork