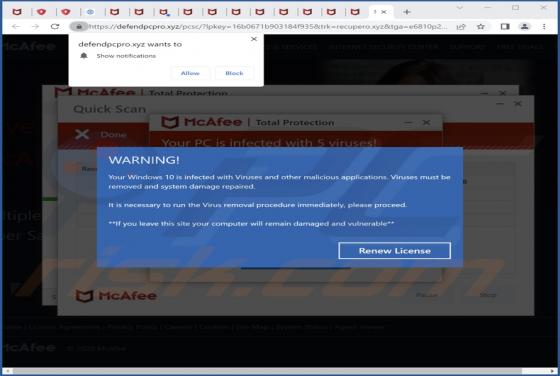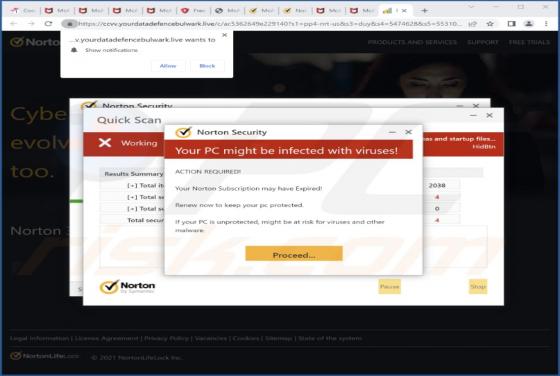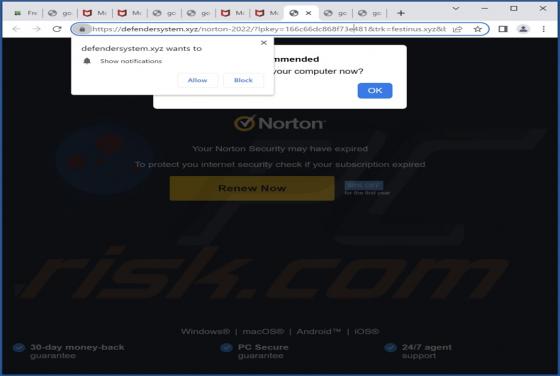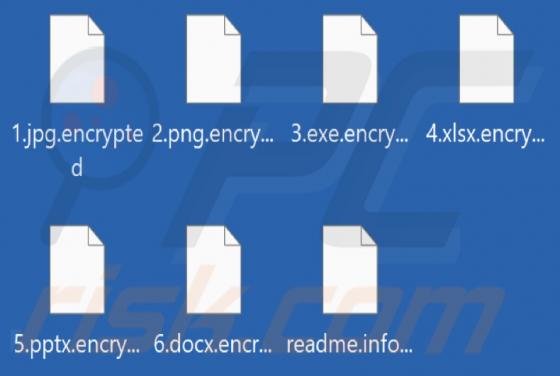
Eyedocx Ransomware
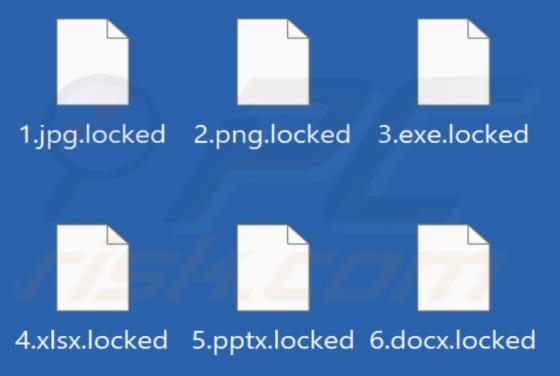
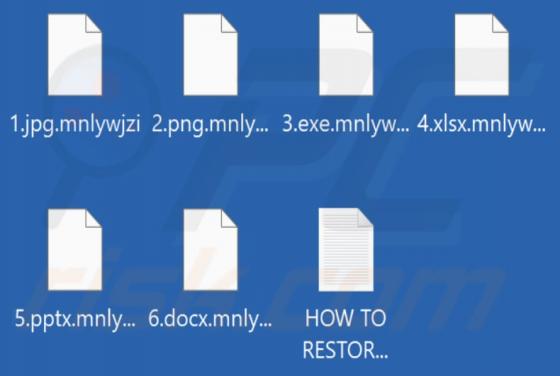
Our researchers discovered the Eyedocx ransomware-type program while inspecting new submissions to VirusTotal. Malware of this kind operates by encrypting data and demanding payment for the decryption keys/tools. When we executed a sample of Eyedocx on our test system, it encrypted files and appe