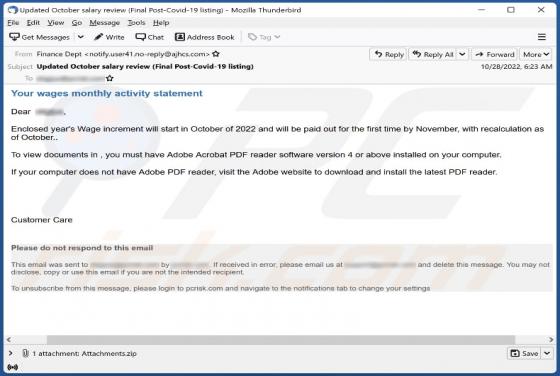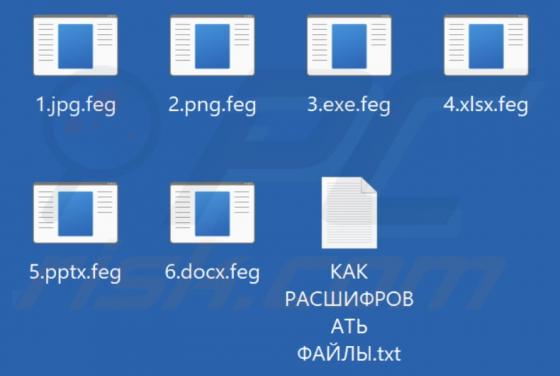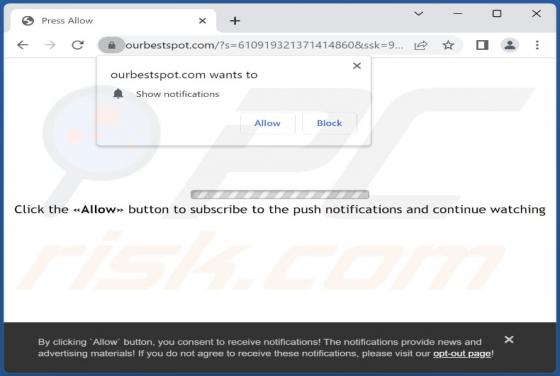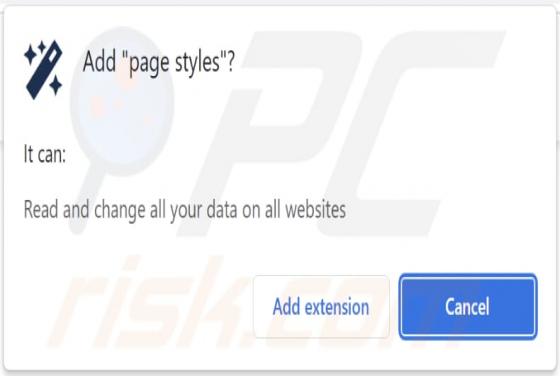
Mobile Apps Group Adware (Android)
Mobile apps Group is an adware family targeting Android operating systems. The name is based on the developer account on Google Play - from which the adware-type apps originate. Said account has been noted for previous questionable/malicious activity and has over one million app downloads to its n