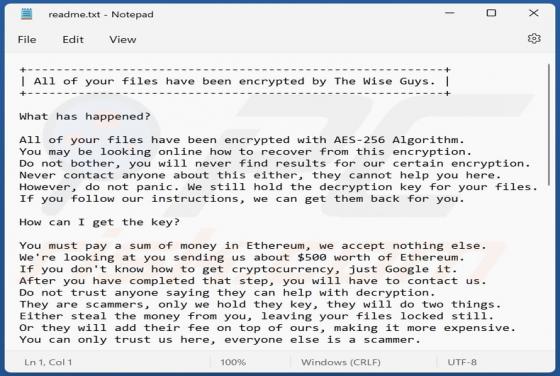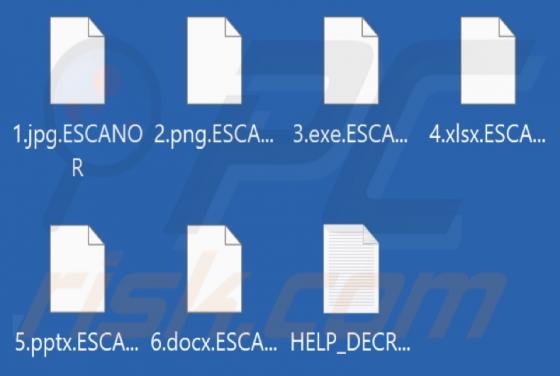
ESCANOR Ransomware
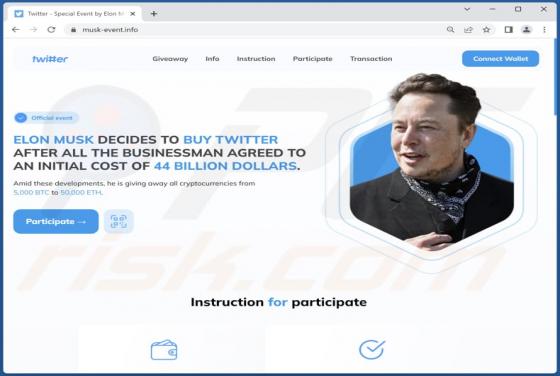
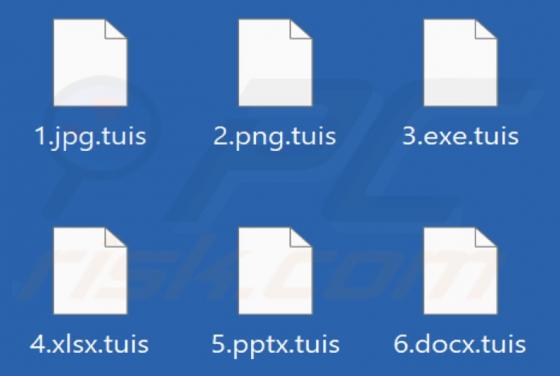
While investigating new submissions to VirusTotal, our researchers discovered the ESCANOR ransomware. It is designed to encrypt data and demand ransoms for the decryption. When we executed a sample of this ransomware on our test machine, it began encrypting files and changed their filenames. To e