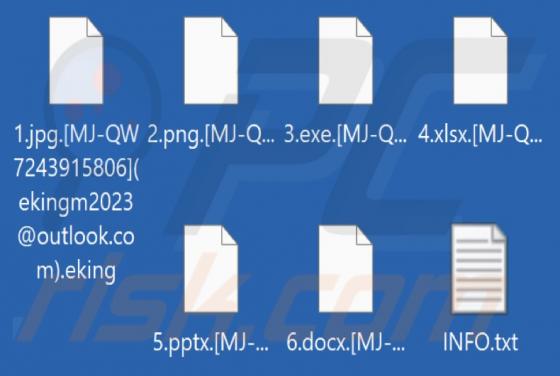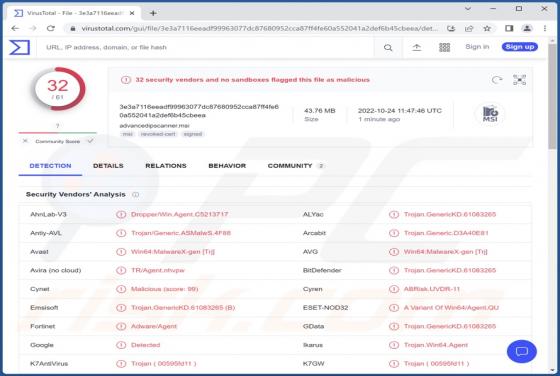
RomCom RAT
RomCom is the name of a Remote Access Trojan (RAT). Malware categorized as such is designed to enable remote access/control over infected machines. RATs can be highly multifunctional and thus pose a wide variety of threats. It is noteworthy that RomCom has been used in attacks against Ukraine's m