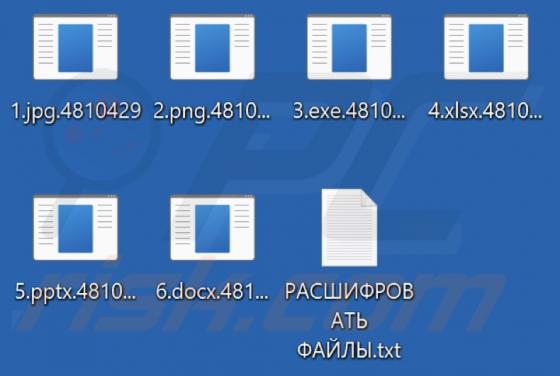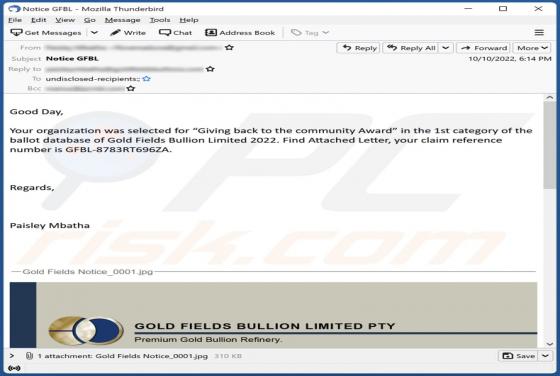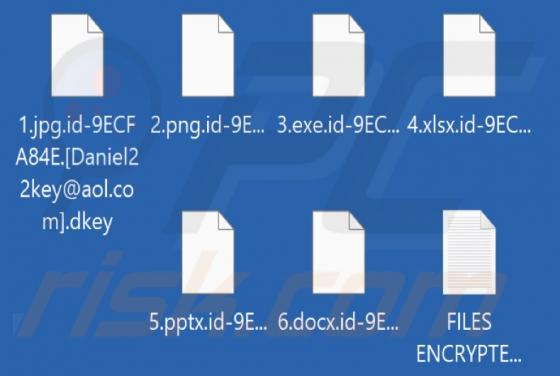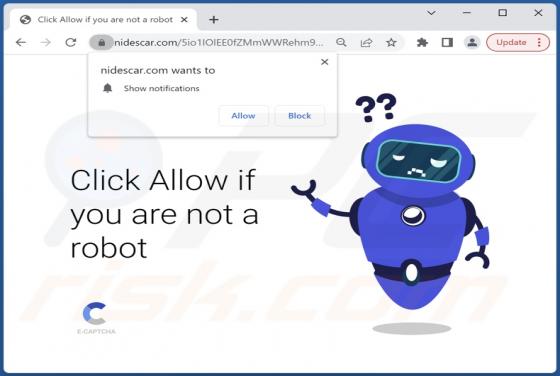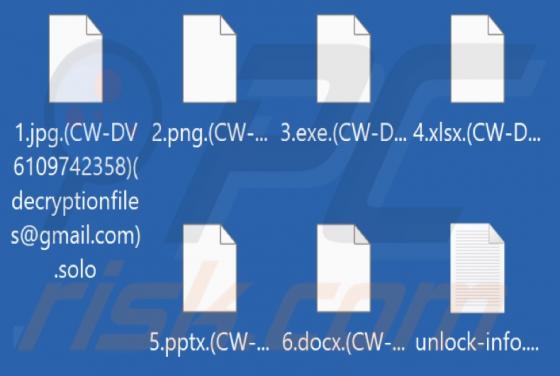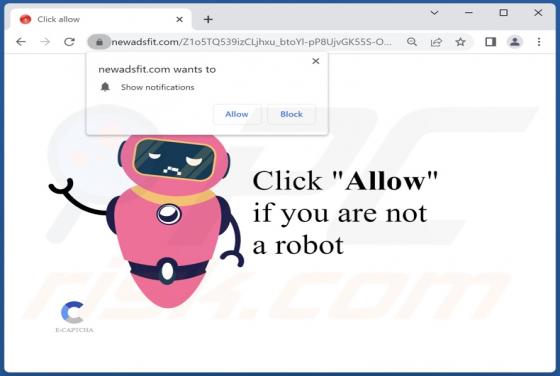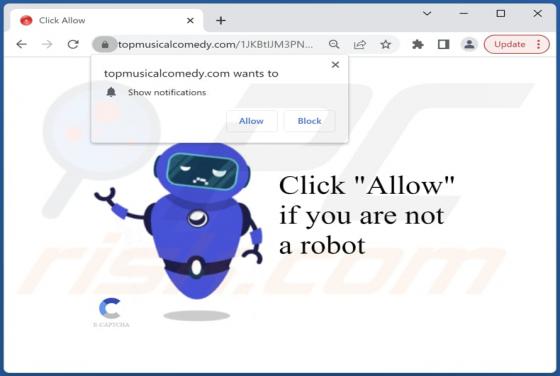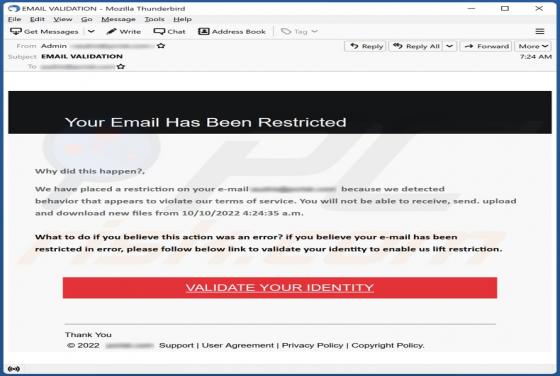
Your Email Has Been Restricted Email Scam
We inspected this email and concluded that the scammers behind it aim to trick recipients into providing them personal information. Emails of this type are called phishing emails. This one is disguised as a letter from an email service provider. It instructs recipients to validate their identity v