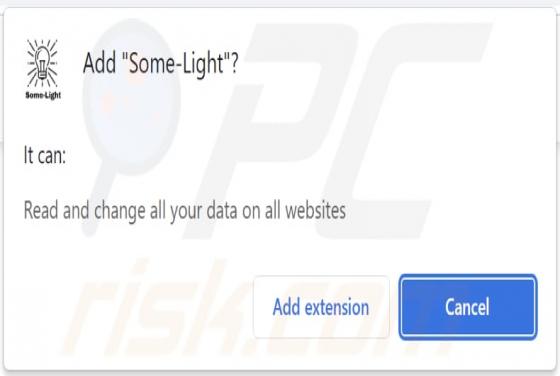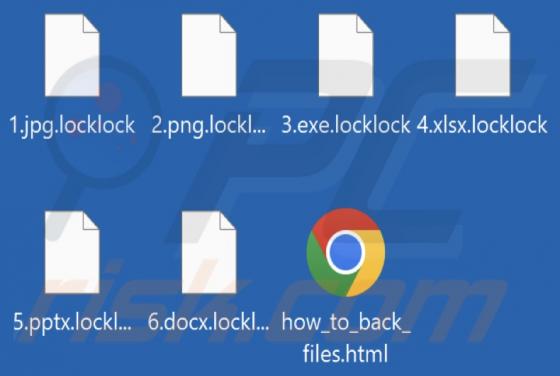
Bruhnet Ransomware
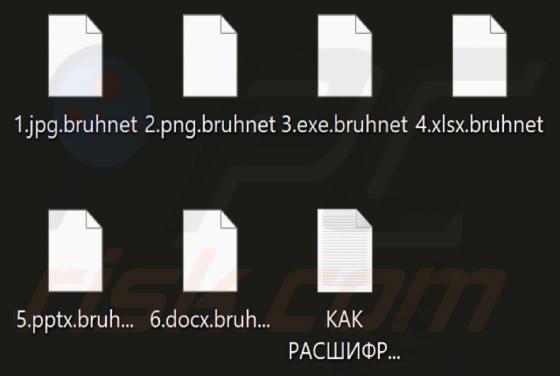
We discovered the Bruhnet ransomware-type program while inspecting new submissions to VirusTotal. This program belongs to the Xorist ransomware family. After we executed a sample of Bruhnet on our test machine, it encrypted files and appended their names with a ".bruhnet" extension. For example,