Extension Settings Browser Hijacker
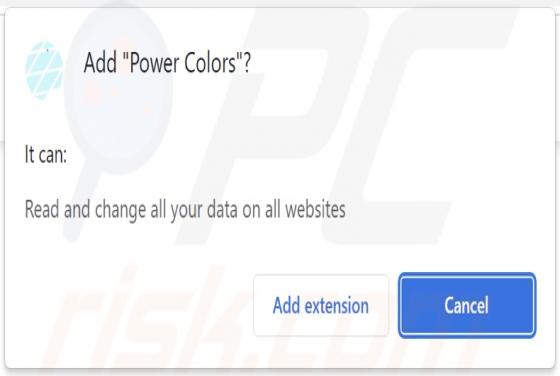
While inspecting scam sites, our research team discovered a rogue installer containing the Extension Settings browser extension. After analyzing this piece of software, we determined that it is a browser hijacker that promotes the ardslediana.com fake search engine. Typically, browser hija