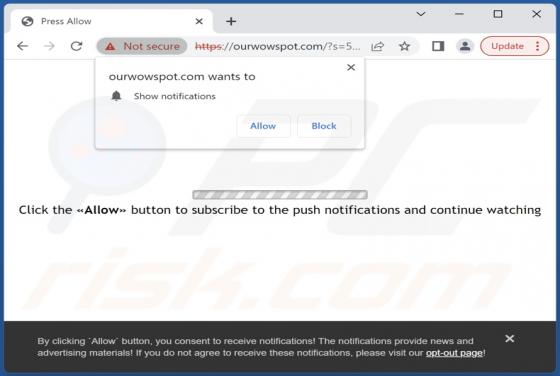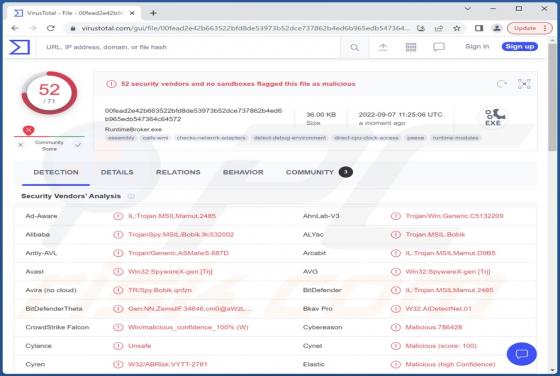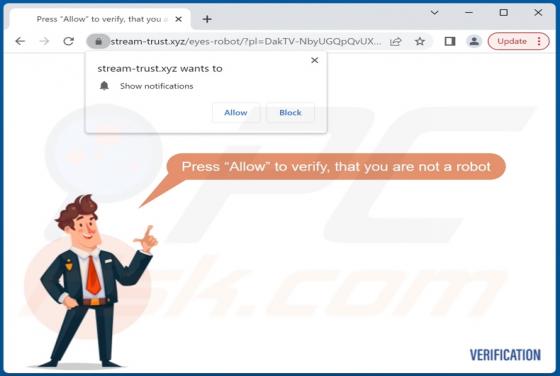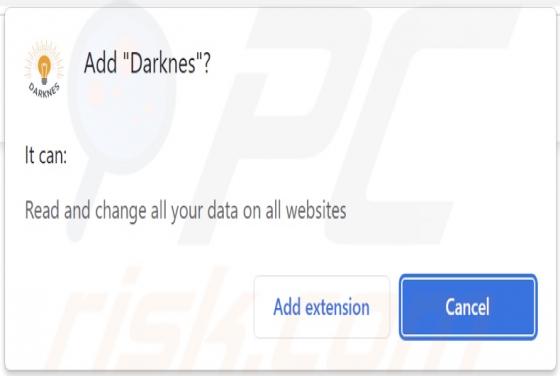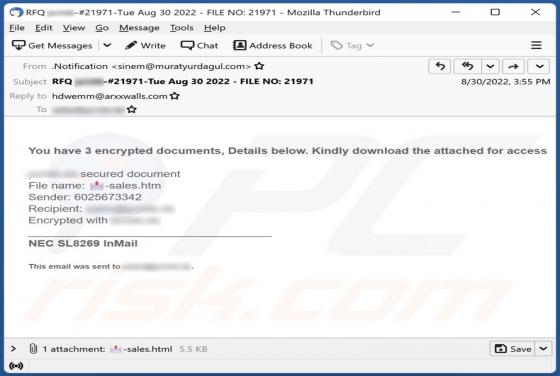
You Have 3 Encrypted Documents Email Scam
After inspecting the "You Have 3 Encrypted Documents" email, we determined that it is spam. Letters of this spam campaign operate as phishing scams. By claiming that recipients have been sent secured files, the mail attempts to trick users into disclosing their email account log-in credentials.