How did ransomware infect my computer?
Introduction
Over the years hackers have used several diverse and innovative ways to infect users with a wide variety of malware strains. Ransomware is no different in the sense that it uses a lot of the same methods employed in other malware attacks. It is still to a large extent dependent on the same rules and methods to infect PCs. This does not mean that the threat posed by ransomware is somewhat reduced because its operators rely on similar tactics, rather these tactics continue to work despite the InfoSec community knowing about them and slack security habits shown from the public at large.
Before a deep dive into how ransomware performs the actual infection of the machine, a quick definition of ransomware is needed. Ransomware can be defined as a family of malware that prevents or limits users from accessing and using the infected machine. This is normally done in two ways by locking the screen or by encrypting files which in turn prevents access until decrypted. The locking of the screen, hence preventing user interaction, has fallen out of favor amongst hackers. This is because crypto-lockers, a general term given to ransomware which encrypts data and files, is far more effective and harder to combat. Both types of ransomware will require the victim to pay a ransom in order to gain access to the encrypted files or the removal of the locked screen.
Of all the methods of infection covered below, a list of how to prevent such an infection will be included as well. These measures do not require a degree in computer science and generally determined by researchers to make up accepted best practices with regards to securing your devices.
Table Of Contents
- Introduction
- Email Attachments
- Remote Desktop Protocol (RDP)
- Malicious URLs
- Malvertising
- Drive-by Downloads
- Targeting Managed Service Providers (MSPs)
- Lateral Network Infections
- Physical Infection Vectors
- Downloading Pirated Content
- Conclusion
Email Attachments
The most common and exploited method of attempting infection with not only ransomware but most forms of malware. In many cases, the humble spoofed email is the first port of entry for personal users and corporate networks alike. When using spam emails hackers use a combination of social engineering tactics to try and trick the end-user into opening the malicious file.
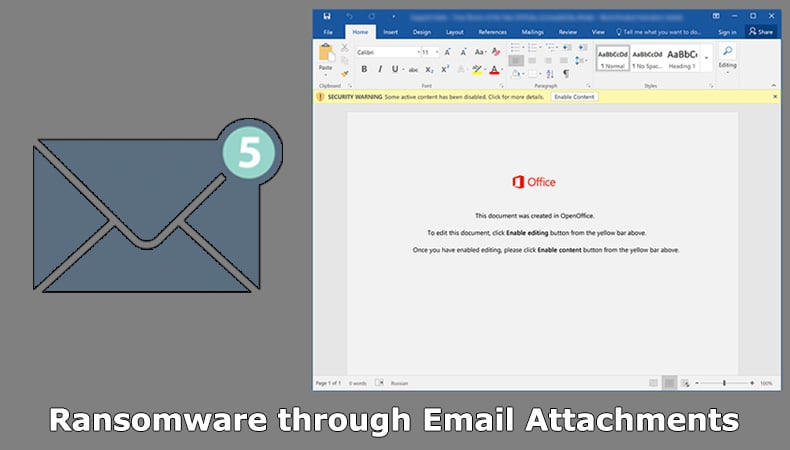
The malicious file can be in a variety of formats, be they ZIP file, PDF, Word document, or Excel spreadsheet. That is by no means an exhaustive list. Even image files can be corrupted to install trojans that can latter download and install ransomware. What makes emails still a valid and incredibly effective threat is the extent to which hackers will compose fraudulent emails that look almost exactly as if sent by the legitimate company been mirrored. Further modern ransomware operators will painstakingly research their targets in order to make it more likely an end-user will click on the malicious file.
How to prevent email ransomware infections:
- Do not open attachments from suspicious addresses.
- Always check the sender's address for subtle spelling errors. This may suggest the email has been spoofed.
- A favored tactic for ransomware operators is to send malicious files that require macros to be enabled. It is advised that end-users should not enable macros as this can allow malicious scripts to be run often without the end user's knowledge.
- It is further advised that individuals and companies install anti-spam filtering software to prevent spam emails from even being received by the user or employee.
Remote Desktop Protocol (RDP)
This is an incredibly popular option for ransomware operators to exploit. Ransomware variants like Dharma and GandCrab are well-known proponents of this attack method. The remote desktop protocol or RDP allows for the connecting of one or more computers across a network. Through this connection, applications can be downloaded and installed. If a hacker is able to exploit this connection then they can run malicious code which for the purposes of this article would mean the downloading and installing of ransomware.
RDP arose from a need for IT administrators to do their jobs over long distances and it is a convenient tool. Sadly, hackers were quick to realize the potential of the protocol as well. Normally RDP requests are handled through port 3389 which means hackers can use a tool known as a port scanner to detect exposed ports. The next phase begins when the hacker attempts to either use known vulnerabilities to gain access or to brute force a massive list of known credentials in an attempt to strike it lucky. Once this is done antivirus software can be disabled, ransomware installed, and a backdoor opened for future attacks.
Securing your RDP can be done by following these security measures:
- Always use strong passwords for RDP credentials.
- Further, it is advised that two-factor authentication is used for RDP sessions.
- By using a VPN it becomes far harder for hackers to find open ports.
- Change the RDP default port 3389.
Malicious URLs
This infection method is closely related to emails, as often rather than a malicious file like a Word document hackers will include a malicious link. The link will then redirect to a download which will then install the ransomware. It is not just emails that are susceptible by social media and instant messaging can be used to distribute the malicious link as well. Again, hackers will employ social engineering tactics to entice or scare the recipient into clicking the link.
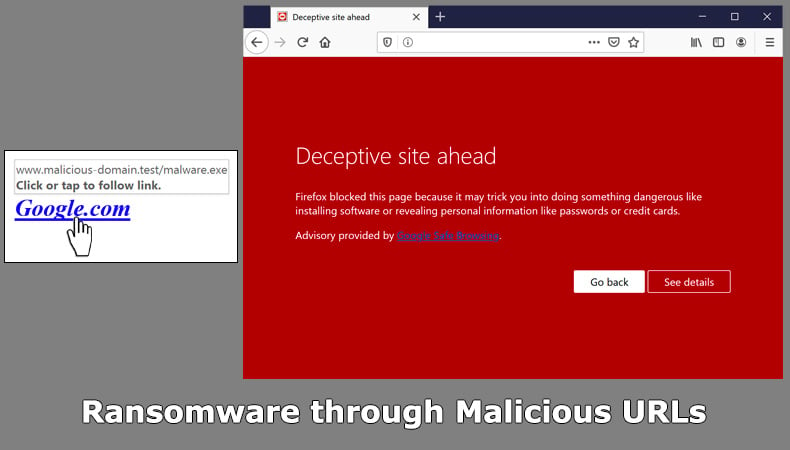
Protecting yourself against malicious links can be done in the following ways:
- Hover over links in emails and direct messages to check the destination before clicking. If it looks suspicious do not click.
- Do not trust any embedded link sent in via email or instant messaging until thoroughly checked.
- Rather than clicking on a link, a user can enter the web address manually or search for the address on a search engine first. This can also help prevent phishing attacks.
Malvertising
In the past Sodinokibi was seen been distributed alongside malvertising campaigns. Malvertising, or malicious advertising, is an attack that involves hackers typically injecting malicious code into legitimate online advertising networks. The code typically redirects users to malicious websites. The malicious website is in turn linked to an exploit kit which is designed to take advantage of a number of known vulnerabilities in either Internet Explorer or Flash to gain access to the user’s machine. From there ransomware, or a whole host of other malware strains, can be installed on the victim’s machine.
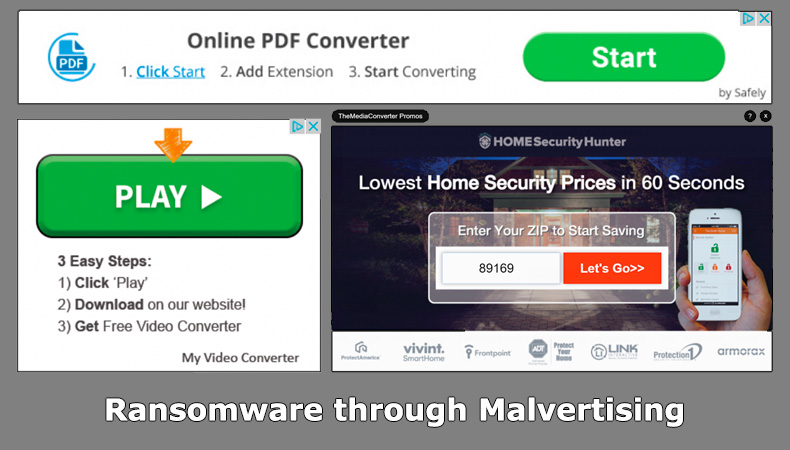
Exploit kits were incredibly popular methods of infecting users with malware when the Internet Explorer and Flash dominated the Internet landscape. There use declined with the popularity of those products. However, exploit kits have seen a resurgence of late as skilled ransomware operators are now targeting large organizations who often run legacy software.
How to prevent falling victim to a malvertising campaign:
- Be sure to keep your operating system and software packages up to date by regularly installing updates if not done automatically.
- Various great ad-blockers are available which can go a long way in preventing users from falling victim to malvertising campaigns.
- Ensure that plugins like Flash and Java are set to click-to-play, this prevents them from running automatically which is what many hackers need to get a foothold on the system.
- Be sure to install and use verified or trusted plugins. Disable plugins not used regularly.
Drive-by Downloads
Drive-by downloads are typically seen as a malicious download that occurs without the end user’s knowledge. This can be done in a similar way to some malvertising campaign, in that the hacker could host a website with malicious downloads and gets victims to download from the hosted website. Another method drive-by downloads can be done is by injecting malicious code into legitimate websites and then use an exploit kit to compromise machines.

What makes drive-by downloads such a threat is that they do not need the end-user for any input. Unlike with enabling macros on Word documents. By simply visiting a website an infection can occur as the malicious content analyses your device for specific vulnerabilities and automatically executes the ransomware in the background.
That does not mean that you cannot defend yourself against drive-by downloads. The following measures prevent drive-by downloads from being a problem:
- Like with defending against malvertising, it is important to keep operating systems and software up to date.
- Uninstall unnecessary plugins.
Targeting Managed Service Providers (MSPs)
Managed service providers have allowed for many companies independent on size to help compete in an incredibly technologically driven global economy. The service providers in order to give a competitive service often require unparalleled access to company networks. This has given hackers an opportunity to compromise the MSP then the clients of the MSP. It is harder for the hacker to do but on slip on the side of the MSP can be dire for not only the MSP but their entire client base. A number of cities in Texas, including Keene near Fort Work, fell victim to this infection vector when the MSP was first compromised. The combined demanded ransom was 2.5 million USD.
In general MSPs and MSSPs (Managed Security Service Providers) have broad and reliable security policies and measures in place. Clients can further insist on two-factor authentication been implemented wherever possible. Further, the MSP and its employees should be aware of the latest phishing campaigns as this is still the favored method of compromise for many hackers.
Lateral Network Infections
Often in movies, computer viruses, now just commonly referred to as malware, is depicted as being able to replicate itself and infect machine after machine like a digital plague. While movies are prone to over-exaggeration for dramatic effect, there is a grain of truth to the idea. Worms, a type of malware incredibly popular in the early 2000s and peaked with Stuxnet, can replicate and spread to other machines without human interaction.
Not until WannaCry made international headlines did ransomware have worm-like capabilities. Leveraging the infamous EternalBlue exploit, this was the first time ransomware was seen moving laterally across networks. This ability to spread through a corporate network, for example, to other vulnerable machines has the ability to grind operations to a halt. Since WannaCry many of the more dangerous and competent ransomware strains have some features to allow for this lateral movement.
The following two measures have been proven to be the most reliable ways to prevent such movement across a network:
- Segment networks as well as heavily restricting administrative privileges to only those who need them.
- Implement a comprehensive backup strategy and practice.
Physical Infection Vectors
Up until now, we have only dealt with methods of infection dependent on the attacker relying on some form of internet connection in order to infect a machine. This physical transfer of data, namely USB and other portable storage devices, presents yet another opportunity for hackers to spread ransomware. The malware could have infected the device without the owner’s knowledge and once inserted into a PC the malware can get to work encrypting the now infected PC.
The following security tips also apply to other forms of malware distributed through physical devices:
- Companies should have strict policies when it comes to employees using their own devices.
- Never plug in an unknown device into your computer.
- Ensure that you have a reputable antivirus suite installed on your computer.
- Refrain from using public devices, such a photo printing kiosks, as these have been targeted by hackers in the past.
Downloading Pirated Content
For those looking to get a software package or their favorite TV series for free, downloading pirated versions has always been an option. An option that comes with a moral choice no doubt but an option none the less. Regardless of the moral implications, there is a very good reason that this is a bad option. Hackers have long been including malware into these downloads. Hackers also follow trends, when Game of Thrones was about to be released, hackers used supposed pirated leaked versions to spread the Bad Rabbit ransomware.

Even the websites used to facilitate pirate downloads have been more susceptible to exploitation by hackers looking to initiate drive-by downloads. Often pirated software includes no way to receive important security updates allowing hackers to exploit already patched vulnerabilities at will. Regardless of where one stands on the ethical debate regarding pirated software, the fact that it is an active target for hackers should be enough not to warrant downloading pirated versions.
Preventing infection via this route involves simply not visiting or downloading from websites promoting pirated content. Further, if a software deal is too good to be true, it is best to leave it alone.
Conclusion
Ransomware continues to be a major threat to anyone who uses a computer or mobile device. Hackers will develop novel and new ways to spread ransomware variants, however, they often rely on the tweaking of the above examples. In defending against ransomware the tips provided not only defend against ransomware but also against the vast majority of other malware variants. Good security practices often involve developing good security habits that compliment security software. This may be a pain at first but can save vast amounts of money in the long run, let alone a lifetime of family memories if it’s your family photos that get encrypted.
