Barnes & Noble Suffer Major Cyber Incident
In a still-developing story, it was reported by Bleeping Computer that Barnes and Noble, the well-known US book retailer, appeared to have suffered a cyber incident of some kind. Barnes and Noble is the largest brick-and-mortar bookstore in the US with over 600 stories spread across the country. Further, the company also operates Nook, the popular eBook and eReader platform. It appeared that something was not right when customers of the company took to social media to complain about service blackouts.
Customers began taking to various social media platforms to enquire, and in some cases complain, as to why certain Nook services were inaccessible on October 10, 2020. Many of the problems reported by customers involved not being able to access their library of purchased eBooks and magazine subscriptions. Often attempts to do so online or on their Nook, customers experienced no joy as the library was coming up blank or they could not log into bn.com. In response to customer complaints, Barnes and Noble took to Nook’s Facebook page to announce that there had been a system failure and that the company was working to restore the services that were affected.
However, on October 14, the company issued a statement saying that the company had suffered a severe network issue and restoring services from backups. Barnes and Noble told Fast Company that,
“We have a serious network issue and are in the process of restoring our server backups. Our systems are back online in our stores and on BN.com, and we are investigating the cause. Please be assured that there is no compromise of customer payment details, which are encrypted and tokenized.”
Whether a severe network issue or a systems failure, an article published by Good Reader cast more doubt on the companies previous statements. The article reported that store managers believed the incident to be a result of a “virus in the networks” which filtered down to physical stores themselves.
The Register reported that the extent of the problem had even spread to some stores cash registers which for a brief time could not be opened by staff. It was only late on Wednesday in an email to customers seen by Bleeping Computer did Barnes and Noble admit that the company had indeed suffered a cyberattack. In the email to customers the company stated,
“It is with the greatest regret we inform you that we were made aware on October 10, 2020 that Barnes & Noble had been the victim of a cybersecurity attack, which resulted in unauthorized and unlawful access to certain Barnes & Noble corporate systems…We write now out of the greatest caution to let you know how this may have exposed some of the information we hold of your personal details,”
Possible Ransomware Attack
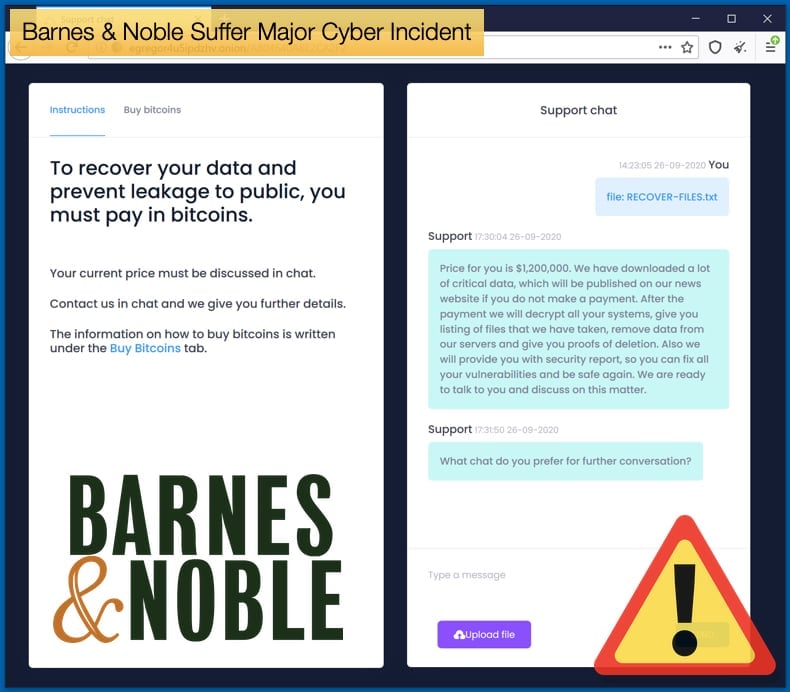
In the space of a few days, the incident went from a system failure to a cyberattack, where initially it was said by the company that no customer data was compromised due to it being encrypted to warning customers their data may have been exposed. Given the mixed messages given by the company, journalists began to dig deeper. In the same email, the company did admit email addresses, billing addresses, shipping addresses, and purchase history were exposed on the compromised systems. The email made no mention of the type of incident suffered by the company, however, several researchers believed that it was most likely a ransomware attack.
This belief was backed by evidence, although saying for certain that it was ransomware without the company’s admission is difficult. Evidence that Barnes and Noble suffered a ransomware attack included the admission that company employees were attempting to restore services from backups, a symptom of a ransomware attack as often victims are forced to restore systems from the backups they made. Ransomware attacks also occur when minimal staff is at work, this often means that attacks occur over weekends when there less staff there is available to detect an attack.
As to whether this counts as actual evidence is surely debatable but Bad Packets had told Bleeping Computer that they had detected several Pulse VPN servers used by Barnes and Noble were vulnerable to CVE-2019-11510. The vulnerability if correctly exploited would allow an unauthenticated attacker network access and allow for remote code execution. Further, the flaw has become increasingly popular amongst major ransomware gangs to gain access to high-value targets. More evidence to suggest that the company did indeed suffer a ransomware attack came in the form of an unrelated data leak containing the credentials to VPN accounts, some of which were traced back to Barnes and Noble.
In a later article published by Bleeping Computer, Barnes and Noble responded to questions put to it by the news site. In response to the incident the company stated,
“As the letter to our customers explains, we closed down all our networks immediately once a cybersecurity attack was suspected. We engaged then a firm of cybersecurity consultants to evaluate the nature of the threat. With their guidance, we have cautiously restored our networks which by its nature has taken time. We acted as quickly as we could given the circumstances and notified customers once we were able to give credible information of what happened. No credit card details are stored on Barnes & Noble systems and therefore the speculation that financial loss from fraudulent activity could result is inaccurate. As of writing, the cybersecurity consultants have detected no evidence of data having been exposed. We have acted therefore with an abundance of caution. We regret sincerely that in so acting we have caused disruption to our customers, especially those of NOOK.”
Egregor claims Responsibility
The latter statement by the company again adds little detail as to the kind of attack suffered or the malware that caused system downtime. However, this is not where the story ends. Bleeping Computer was contacted by a threat actor claiming that it was a very new ransomware gang that was responsible for the attack. That gang is known to distribute the Egregor ransomware variant with operations dating back to September of this year. The threat actor who contacted Bleeping Computer claimed the company network was originally breached by threat actors who gained access via a Windows domain administrator account stole unencrypted "financial and audit" data from their systems.
Access to the compromised network was then handed over to another threat actor who encrypted company data. Tactics like this are on the rise and “initial access brokers” have been seen to partner with ransomware gangs, either to sell network access or to become affiliates of the gang.
To add veracity to the threat actors claim, the gang operating Egregor published data allegedly belonging to Barnes and Noble on October 20. Strangely, rather than data what was published was two Windows Registry hives that appear to have been exported from Barnes & Noble's Windows servers during the attack. This does corroborate the belief that Barnes and Noble suffered a ransomware attack by those behind Egregor, but it does not prove it behind a shadow of a doubt. The release of data after a ransomware attack has become 2020’s main ransomware trend started by the Maze ransomware gang, so Egregor’s actions are in line with current trends dominating the threat landscape.
In a separate incident, Egregor is responsible for attacks targeting two major games developers Ubisoft and Crytek. With regards to the Crytek incident, the company confirmed it had suffered a ransomware attack with leaked data, some 380 MB, been released of Egregor’s leak site. The leaked data contained information and data relating to several games either developed or were canceled during development. Data also contained network information about the company.
With regards to Ubisoft, via the ransomware gangs leak site, the gang claims to have stolen the source code for Watchdog: Legions, a highly anticipated game still set for release. To prove this claim, the gang released 20 MB of data it says are game assets. At the time of writing Ubisoft had made no statement either confirming or denying that they had suffered a ransomware attack. It should be noted that the game assets themselves do not prove beyond a shadow of a doubt that Ubisoft did indeed suffer a ransomware attack.
As with the Barnes and Noble incident and the Ubisoft incident, more information is needed that proves Egregor was behind both attacks. More often than not many are forced to piece together bits of evidence as a detective would. This could be avoided if companies would make statements to confirm such events if they took place.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion