CD Projekt Red suffers Ransomware Attack
The Polish game developer, best known for the Witcher 3 and Cyberpunk 2077, has recently taken to Facebook and Twitter to confirm that they had suffered a ransomware attack. The game developer has recently been in the news a lot following the shambolic release of Cyberpunk 2077, and for none of the reasons the company would like to be in the news. Suffering a ransomware incident now would be the last thing company employees and executives would want to deal with. This is also not the first time the company has suffered such an incident.
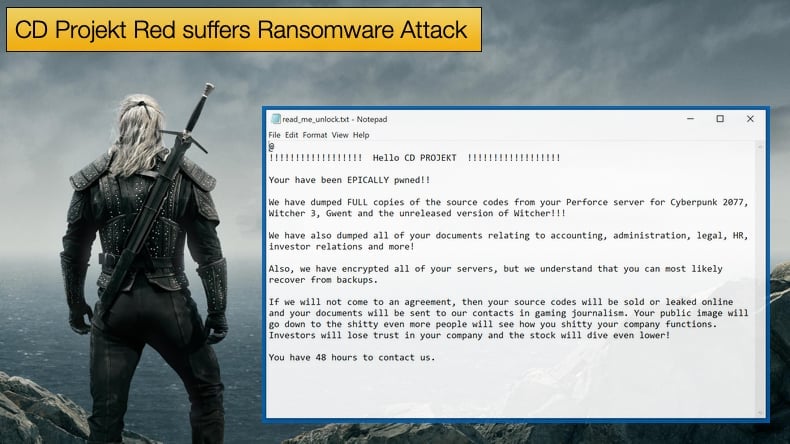
The latest incident was confirmed on February 8, 2021, via a statement. Included in the statement was a copy of the ransom note dropped by the attacker. In turn, hackers responsible for the attack claim, based on claims made in the ransom note, that source code for games like Cyberpunk 2077, Gwent, and The Witcher 3, along with an unreleased version of The Witcher 3 game, had been successfully stolen. Such tactics are in line with double extortion tactics which now dominate the ransomware threat landscape.
Despite efforts from the hackers to exert extra pressure on the game developer, CD Projekt Red have stated,
“We will not give in to the demands nor negotiate with the actor, being aware that this may eventually lead to the release of the compromised data…We are still investigating the incident, however at this time we can confirm that —to our best knowledge — the compromised systems did not contain any personal data of our players or users of our services.”
CD Projekt Red is just another game developer to have been targeted by ransomware operators. Those behind the Egregor ransomware strain successfully attacked both Ubisoft and Crytek applying the same double extortion tactics of stealing data before encryption then threatening to release the data if the ransom is not paid. Included in this list is Capcom who suffered an attack by Ragnar Locker. Over the years not even game developers have been spared from ransomware gangs.
With the increasing popularity of gaming, in general, comes with the potential to make impressive sums of money, with success and hype comes a lot of attention some of it unwanted. For developers that specialize in online games the threat faced may be more severe in that a ransomware attack could force the game to go offline while the company attempts to recover from the incident. This can create the potential for the increased loss of earnings that will apply more pressure to the victim to pay.
HelloKitty Ransomware the Culprit
With CD Projekt Red’s posting of the ransom note, security researchers had a massive clue as to which ransomware gang may have been behind the attack. According to Fabian Wosar of Emisoft, the offending piece of ransomware is HelloKitty. This also put to bed that the ransomware attack was done by a disgruntled gamer, as HelloKitty is operated as a for-profit ransomware strain. While assumptions as to the offending strain of ransomware have been made based on the ransom note, it should be cautiously noted that to 100% confirm that it is HelloKitty security researchers would need to see the actual code. However, the ransom note does provide more than a few clues as to who was responsible.
Assuming that it is HelloKitty, the ransomware’s operators have been extremely active since the last few months of 2020 and into the start of 2021. The last attack reported other than CD Projekt Red involved an attack on a UK Healthcare organization at the end of January 2021. While it is irresponsible to attack healthcare facilities during a global pandemic, HelloKitty is not the only ransomware gang to do so. Those behind HelloKitty seemed to determine to ruin Christmas for at least two organizations. According to security firm Cado, Brazilian powerplant operator CEMIG suffered an attack. The incident was confirmed by CEMIG with the powerplant operator stating,
“CEMIG informs that on December 25, 2020, the SOC (security operation nucleus) detected anomalous behavior on the internal network, with characteristics of a malicious ransomware attack. The teams responsible for the correct detection of the attack and subsequent adoption of the containment measures were immediately activated. Less than 10% of servers on the Windows / Microsoft Hyper-V platform had their content encrypted. Workstations have also been partially compromised and are in the process of being verified. It is important to highlight that, thanks to the fast and effective containment action carried out by Cemig, the operation of the electrical system and the main databases (customers, billing, customer service, and business management) were not compromised, thus guaranteeing the provision of services to our clients.”
The statement regarding the Hyper V platform by CEMIG matches the ransom note seen by Cado regarding the attack. According to Cado, a French IT company, whose name was redacted from the ransom note also suffered an attack on Christmas day. However, it is the attack on CEMIG that may be the most worrying as the ransomware contains a list of processes it terminates before encryption. In the list, several processes are related to Industrial Control Software processes meaning that the ransomware is more than capable of going after networks used to maintain infrastructure relating to electrical supply, water and sanitation, and numerous other industrial applications.
The list appears to have been copied directly from the MegaCortex ransomware, when the list was first discovered researchers were quick to note that this should come as a concern to organizations dependent on industrial control systems like SCADA. It needs to be noted that at the time of discovery the ransomware was more focused on terminating processes that might hinder encryption rather than targeting SCADA processes directly.
In defending against HelloKitty and ransomware in general, Cado Security advises:
- Consider utilizing separate IT systems (privileged access workstations) for use by network and system administrators. For these systems, utilize additional two-factor authentication and ensure there is no direct access to the Internet.
- Consider employing an “allowed list” to restrict server outbound communications to IPs / Domains that they need access to.
- Consider storing backups of key business and critical IT infrastructure systems e.g. ActiveDirectory, off of your network.
- Avoid opening up RDP services to the internet, if it's required consider using an ALLOW LIST approach only, and DENY all unknown IPs by default.
- Ensure you can restore to a segregated network environment.
- Ensure you have tested the restore capabilities of your backups.
Industrial Targets
Not to take anything away from the seriousness of the incident impacting CD Projekt Red and the increase in game developers falling victim to ransomware, but there has also been an increase in industrial sectors being targeted. In a report published by Digital Shadows, industrial good and services amounted for 29% of reported attacks in the third quarter of 2020. One of the reasons behind this is that industrial services may feel extra pressure to pay when the service they are contracted to provide cannot be done as ransomware caused a shutdown of services.
Further, systems used by the sector are in constant use. This creates another problem in that operators may be reluctant to take them offline to apply the steady flow of routine software patches necessary to protect against security vulnerabilities that can give ransomware gangs access in the first place. That's if the machines can receive security updates at all because obsolete, unsupported technology is still common in many industrial environments. The combination of constantly running software that may very well be obsolete makes the entire sector ripe for exploitation by ransomware gangs.
The stats put forward by Digital Shadows seems to personify reasons why MegaCortex has included industrial control processes in its termination list. When this is combined with the reality of obsolete and always running software to meet the publics' demand it is little wonder HelloKitty is looking to get in on the action.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion