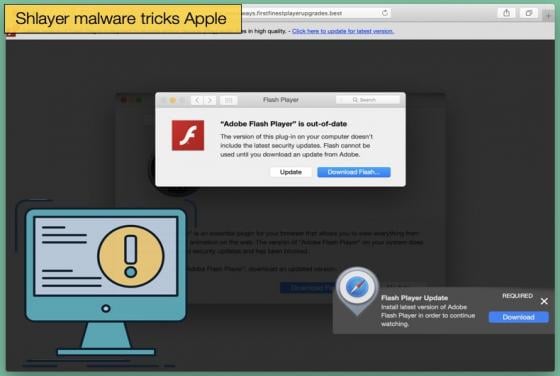
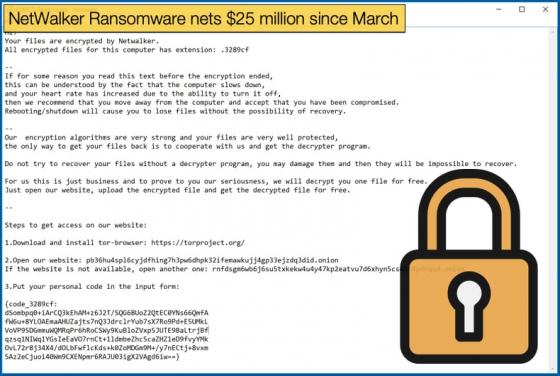
New Python Malware targeting FinTech Companies
Researchers based at cybersecurity firm Cybereason, have uncovered a new malware been deployed by a well-known and seemingly well-resourced hacking operation codenamed Evilnum. The group has been deemed an advanced persistent threat and has been operating since 2018. Past research published by ESET