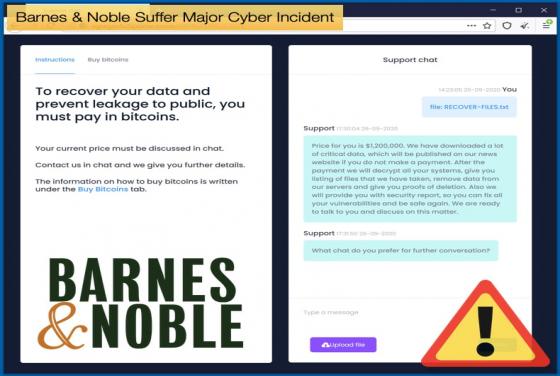
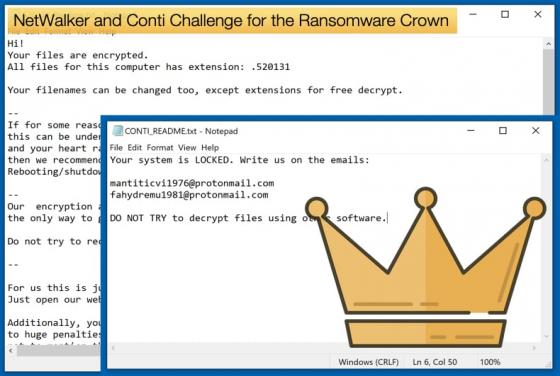
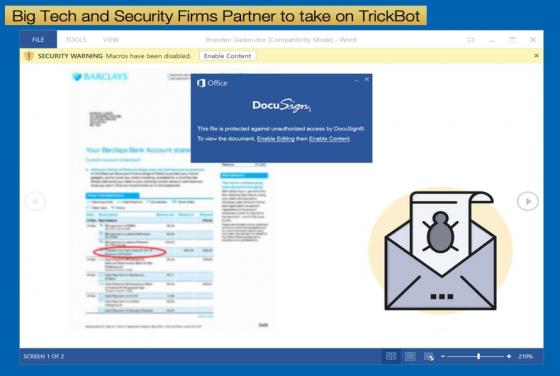
Data Breaches and Extortion
Two recent instances of data breaches have shown the dangers of what stolen data can do in the wrong hands. The first of which impacted a Finnish psychotherapy clinic. The clinic suffered a breach two years ago, with the results of the breach only making themselves known now. A threat actor is deman