Phorpiex seen Spreading another Ransomware
The last time this publication covered Phorpiex it was seen distributing the Nemty across its botnet infrastructure. In the past the botnet was seen distributing GandCrab, however, researchers discovered that the botnet was seen distributing a new ransomware called Avaddon during the preceding month of June 2020. Avaddon’s distribution was discovered by Proofpoint who likewise noted that several other older ransomware strains were being distributed in separate campaigns but at roughly the same time.
In a separate report published by Check Point, it was revealed that the recent surge in Phorpiex activity amounted to the botnet being one of the most active malware families for the month of June. In the month of May, the malware was ranked 13th in terms of activity, the botnet climbed the rankings in June to be the second most detected malware family. The first was Agent Tesla which has been described by researchers as,
“Agent Tesla is an advanced RAT functioning as a keylogger and information stealer, which is capable of monitoring and collecting the victim’s keyboard input, system clipboard, taking screenshots, and exfiltrating credentials belonging to of a variety of software installed on a victim’s machine (including Google Chrome, Mozilla Firefox, and Microsoft Outlook email client).”
The primary method Phorpiex uses to distribute malicious payloads, including Avaddon and the other ransomware strains it has partnered with in the past is via phishing emails. While unsophisticated it still can be an incredibly effective technique, particularly when the botnet is capable of sending an email to thousands of addresses.
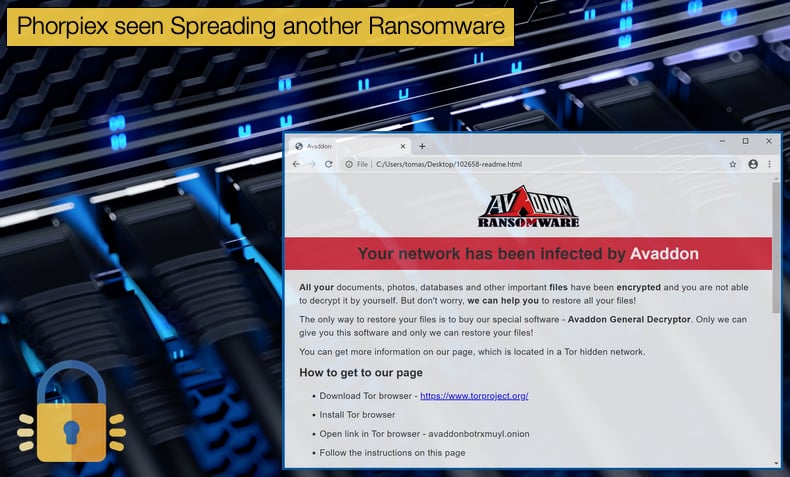
In the campaign distributing Avaddon, the email contained a zip file with a wink emoji as the subject line. Check Point researchers warned businesses and end-users to take the following precautions,
“Organisations should educate employees about how to identify the types of malspam that carry these threats, such as the latest campaign targeting users with emails containing a wink emoji, and ensuring they deploy security that actively prevents them from infecting their networks,”
Phorpiex and Sextortion Campaigns
Not only does Phorpiex partner with ransomware partners by it has been a major contributor to recent sextortion campaigns. Typically such a campaign involves the mass distribution of emails which claim to have pictures or video of the victim watching pornography or some other compromising position the victim may feel embarrassed about. The victim is then asked to pay a certain amount and the supposed picture or video in the scammer’s position will not be released to social media. In the vast majority of these cases, it is important to note that the scammer is in possession of no compromising material. In 2018 the FBI’s Internet Crime Complaint Center reported a 242% rise in extortion emails, the majority of which are “sextortion”, with total losses of 83 million USD in reported crimes. As to the numbers regarding unreported crimes, they are anyone’s guess, but it is safe to assume that the total loss suffered by victims would cause the reported figure to skyrocket.
Distribution of the spam emails is typically done via botnets, meaning anyone with a router may have unknowingly sent such an email in the past if the router or other Internet of Things device formed part of the botnet. In the case of Phorpiex, email addresses are randomly chosen from a downloaded database and emailed. The botnet is capable of sending 30,000 messages like this in an hour. In order to try and convince receivers that they have been compromised and more importantly caught in a compromising position the database used includes both usernames and passwords. These are not obtained by the scammer but as a result of data dumps resulting from previous major data breaches.
It has been mentioned previously that these are not sophisticated but a cunningly crafted campaign can rake in dollars over a period of a few months. Researchers pointed out that one campaign in 2019 brought in 14 Bitcoin, approximately 130,000 USD at the time of writing. The same researchers stated that,
“Given the number of incoming transactions to these wallets, we can also estimate the total number of victims affected by this campaign. Therefore, we can conclude that approximately 150 victims paid the blackmail demand over a span of five months. Considering the number of emails that the spam bot is capable of generating, despite the low numbers of payments received, this still means this simple scam technique was successful. On the other hand, passwords from leaked databases, such as those used in the sextortion campaign, are most often not related to victims’ email accounts. Therefore, the value of this data is quite low. Such databases are sold at a low price, or may even be freely accessible. The Phorpiex actors came up with a method of using such low-quality data to earn a respectable amount of profit.”
Phorpiex coupled with Ransomware
Phorpiex, sometimes also referred to as Trik, has shown on a number of previous occasions what can happen when it partners with known ransomware families, Nemty and GandCrab partnering with the botnet previously. That being said, the new partnership with Avaddon illustrates the botnet’s capabilities, researchers discovered that approximately a million messages were sent by the botnet with the ransomware as the payload during the period from June 4 to June 10. On June 6, 750,000 of that batch of a million were sent in that one day. Based on who received the emails with the malicious payload the primary targets of the campaign were in the manufacturing, education, media, and entertainment sectors.
The use of a botnet for mass distribution is interesting in that for the most part ransomware operators have adopted different tactics in recent years. What is now called “human-operated” ransomware sees ransomware operators going after very specific targets, namely large organizations who can pay higher ransoms, especially when compared to end-users and smaller organizations. This targeted approach often relies on specially crafted phishing emails sent to the target or the scanning for vulnerable internet-facing RDP connections. What these ransomware families, including Ryuk and Sodinokibi, do not do is use mass email campaigns like Avaddon. The use of such campaigns was seen to be an old tactic used when ransomware was in its infancy.
Avaddon adopts other tactics eschewed by the class of “human-operated” ransomware, namely the ransom demanded. According to the ransom note dropped by the malware after file encryption takes place, the victim must pay 800 USD worth of Bitcoin via a TOR browser link and instructions on how to download a TOR browser. Other ransomware operators keen to target Fortune 500 companies will demand hundreds of thousands of dollars to decrypt data. Some are even brazen enough to demand millions of dollars to decrypt data and this must be done in a limited time frame otherwise company data will be leaked to the public or sold to the highest bidder. Avaddon again adopts tactics more closely related to ransomware campaigns three years ago where WannaCry was spread on mass, as an example.
The most recent Avaddon campaign had other tricks up its sleeve to get users to open the email. Other than the suggestive smiley in the subject line, the email contains other sentences designed to get the user to open the .zip file. These include:
- Look at this photo!
- Photo just for you
- You look good here
- I love this photo
- I like this photo
- Is this your photo?
- Is this you?
- My favourite photo
- You like this photo?
Similar tactics have been seen in previous sextortion campaigns in order to grab the user’s attention and this may be just another example of those behind Phorpiex having a unique understanding of human psychology and social engineering tactics. Avaddon is recognized as a Ransomware-as-a-Service so it is highly likely that those behind Phorpiex have come to some sort of agreement, perhaps actively distributing the ransomware themselves rather than simply hiring out their botnet. As with all things cybercrime-related they are often hidden behind smoke and mirrors. It takes dedicated teams of professionals to unravel the complex knots, which can take years in some cases to fully reveal the how, when, and why of a particular cybercriminal gang.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion