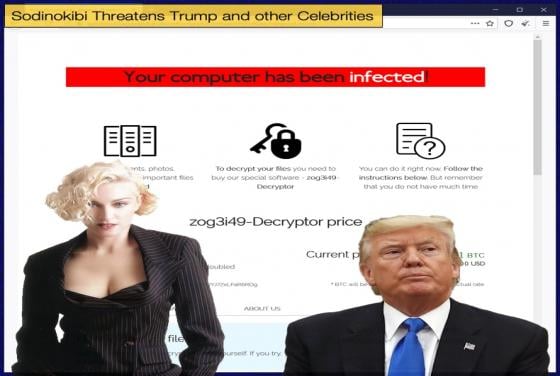
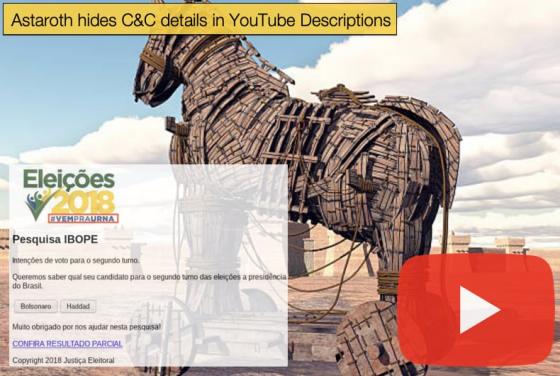
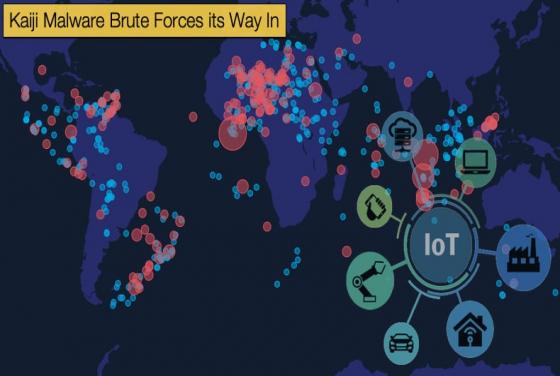
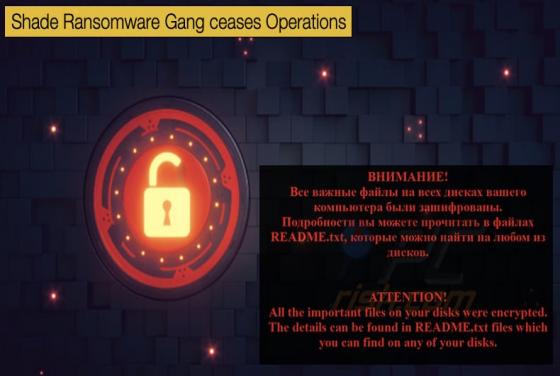
Google releases Data concerning Government-Based Disinformation Campaigns
2020’s news cycle has already been exhausting to follow. For the InfoSec community, the COVID-19 pandemic brought with it a mass of malware campaigns looking to exploit the pandemic as a lure. Silent Night, Astaroth, Zeus Sphinx, and a vast number of other known malware threats have emerged looking